Cybersecurity in the Boardroom: Key Insights from the FrontierZero CISO Roundtable
Our closed-door CISO roundtable in Dubai highlighted a major shift: the perimeter is gone, and real-time identity behavior now defines effective security.

On October 14, 2025, FrontierZero hosted a closed-door CISO roundtable at the Dubai International Financial Centre (DIFC), bringing together security leaders from the finance, consulting, healthcare, and technology sectors. The session, facilitated under Chatham House Rules by Philip Westgarth (Cybersecurity Leader in the Gulf financial services sector), focused on the growing challenges surrounding third-party identity risk, SaaS visibility, Shadow IT, and the rapid emergence of agentic AI systems.
Although a few weeks have passed since the discussion, the themes raised have only become more urgent as organizations accelerate SaaS adoption and begin experimenting with autonomous AI systems in production environments.
What emerged was a clear consensus: traditional perimeter-based security models and static reporting practices are no longer sufficient. Identity has become the new security boundary, and real-time behavioral visibility is now essential for risk management.
The Expanding Supply Chain and Third-Party Risk
Organizations today operate within increasingly complex partner ecosystems. It is now common for large enterprises to maintain relationships with thousands of external vendors, suppliers, contractors, and offshore service partners. This offers agility, scalability, and specialized capability, but dramatically increases exposure.
In 2025, approximately 30% of data breaches involved third parties. Double the rate of the previous year. Participants expressed concern that while internal access controls have improved, visibility into contractor and vendor activity remains limited.
Access reviews are typically static, periodic, and compliance-driven. As a result, unauthorized access or credential misuse can occur in the long intervals between checks.
The discussion highlighted the need to move from a model of one-time credential validation to continuous monitoring that accounts for how identities behave, not just whether they can log in.
Case Study: Qantas and the Importance of Behavioral Context

The June 2025 cyberattack on Qantas Airways served as a central reference point. In this case, the airline’s core infrastructure was never breached. Instead, attackers impersonated IT staff and convinced employees at an outsourced call center to reset authentication credentials. This granted the attackers access to a third-party Salesforce environment containing customer records.
What made the incident particularly noteworthy was not only the method of access, but what was missed.
The compromised identity usually worked from Manila using a specific workstation during normal local business hours. During the breach, system access occurred from a different device, at a different time, likely from a different region.
However, because the security model only focused on whether the credentials were valid, not whether the behavior was normal, the intrusion continued undetected long enough for 5.7 million customer records to be exposed.
The incident highlighted a structural problem: organizations often know who is allowed into their systems, but lack insight into whether the access being seen is expected, typical, and safe.
Identity as the Modern Security Perimeter
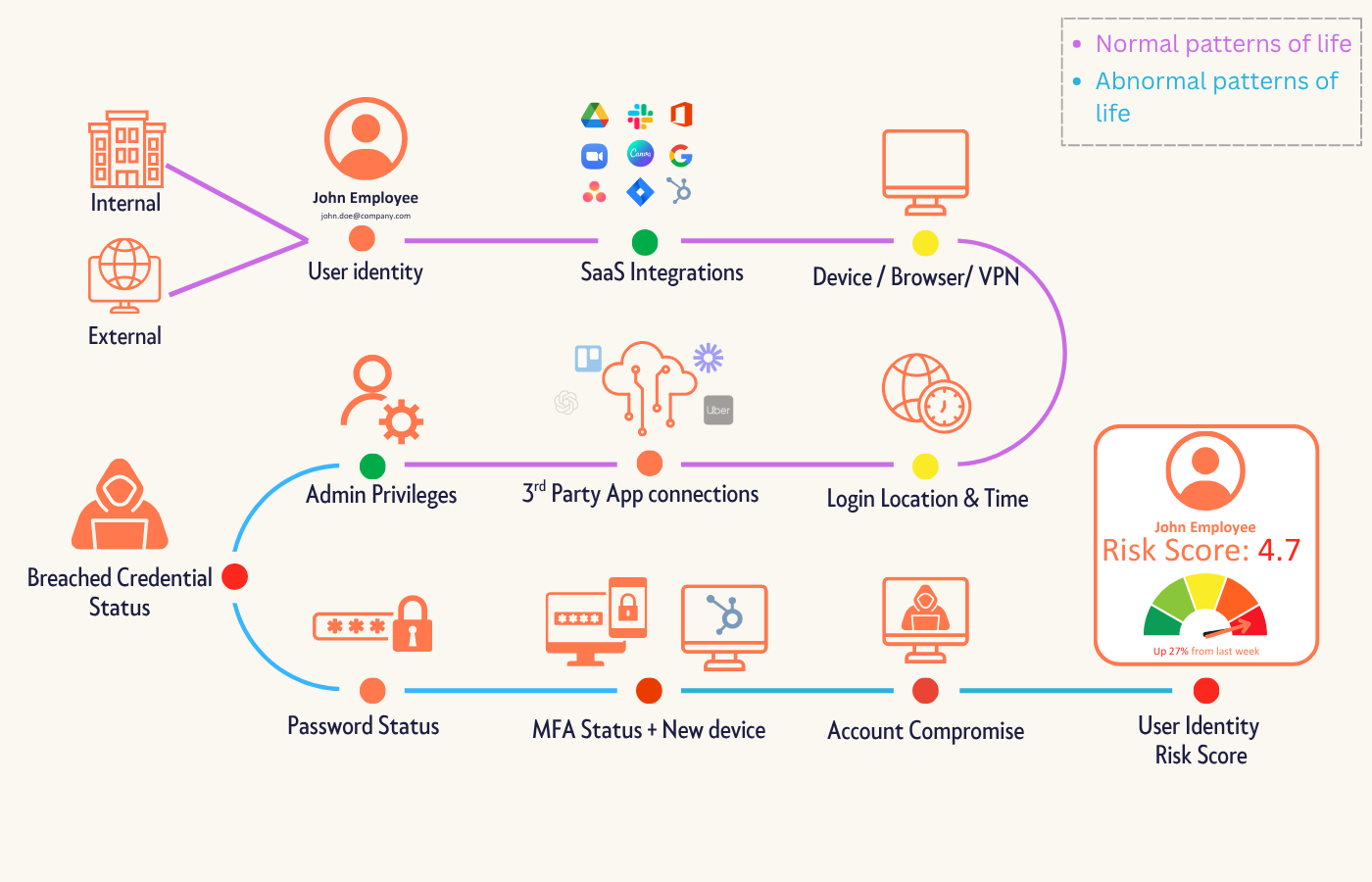
Roundtable participants agreed that identity is now the primary security control plane. This includes not only employees, but also contractors, vendors, machine accounts, API tokens, service accounts, and increasingly, autonomous AI agents.
Effective identity security requires understanding the “pattern of life” for each identity:
- What device do they typically use?
- From what geographic region?
- During what working hours?
- With what normal depth of system access?
- How do they interact with applications and data under ordinary conditions?
When these established patterns change, systems need the ability to detect anomalies in real time and respond automatically. This represents a shift from access validation to contextual access governance.
Shadow IT and SaaS Complexity

The group also examined the growing challenge of Shadow IT and SaaS sprawl. While enterprises may officially track around one hundred approved SaaS applications, studies show the real number in use is often closer to a thousand. Many of these are introduced not through malicious intent, but to fill operational needs faster than internal IT processes allow.
However, these unmanaged tools often operate outside established authentication workflows, logging controls, and data governance mechanisms. The result is fragmented identity data, unmonitored access paths, and difficulty maintaining compliance with frameworks such as NIS2 or DORA.
Participants agreed that security teams must pair governance with enablement. Simply blocking tools drives workarounds; understanding why certain tools are adopted allows for safer, sanctioned alternatives and structured integration.
The Rise of Agentic AI and the Assurance Gap
Another major topic was the increasing adoption of agentic AI — systems capable of planning, executing, and adapting tasks independently. Gartner estimates that one-third of enterprise applications will include agentic AI by 2028. While this has the potential to improve efficiency, reduce operational overhead, and enhance customer service, it also introduces risks that traditional governance models are not yet designed to manage.
One emerging challenge is prompt injection, where malicious inputs are crafted to cause an AI agent to leak data, alter decisions, or perform unauthorized actions. Unlike SQL injection, prompt injection requires no programming skills, only carefully worded language. This dramatically lowers the barrier for exploitation.
The discussion noted that many organizations are deploying AI faster than they are implementing controls such as clear ownership, role-based agent permissions, or continuous behavioral oversight. There is a growing urgency to formalize AI assurance and accountability frameworks before agent adoption accelerates further.
Moving from Static to Living Security Policies
A recurring theme throughout the roundtable was the inadequacy of static documentation-based security. Policies, procedures, and vendor risk reports are often treated as compliance artifacts rather than tools for real-time operational defense. Participants agreed that organizations need living policies supported by:
- Continuous monitoring
- Automated enforcement of controls
- Real-time policy condition evaluation
- Dynamic risk scoring
- Integrated audit trails
This shift mirrors the broader transition from periodic assessment to continuous security verification.
Key Recommendations for Security Leaders
- Implement pattern-of-life identity monitoring across both internal and third-party accounts.
- Shift from point-in-time reporting to continuous oversight of contractor and vendor access.
- Surface and rationalize Shadow IT, aligning usable workflows with secure alternatives.
- Establish AI assurance frameworks early, before agent usage scales.
- Adopt Security by Design, embedding controls at the system architecture stage rather than post-deployment.
Conclusion
The FrontierZero CISO Roundtable underscored a structural shift in how organizations must approach cybersecurity. As supply chains grow, SaaS ecosystems expand, and AI systems begin to operate autonomously, identity behavior has become the most reliable indicator of security risk.
Preventive security now depends on continuous context, real-time monitoring, and governance frameworks capable of adapting as quickly as modern systems evolve.
We will continue this discussion at our next invitation-only roundtable later this year.
Security leaders interested in participating or contributing topic recommendations are welcome to reach out at [email protected].




