Configuration Drift: The Quiet Risk Hiding in Your SaaS Stack

What Is Configuration Drift?
In fast-moving SaaS environments, even small changes can quietly shift your security posture from "safe" to "vulnerable."
Configuration drift happens when the settings in your SaaS apps change over time—either manually, automatically through updates, or via integrations—and no one notices. A misconfigured permission here, a toggled-off setting there, and suddenly your environment no longer matches your policies or best practices.
Why It Happens More Than You Think
SaaS platforms are constantly evolving. New features roll out. Admins adjust settings. Apps integrate with one another. And not every change gets documented or reviewed.
Without centralized oversight or change management, it’s easy for configuration drift to slip in unnoticed.
Some common examples:
- A file-sharing app disables MFA after a new update
- A departing admin turns off access controls to troubleshoot an issue
- A new integration overrides default security settings
- An unused app keeps running with excessive permissions
These small drifts create risk—especially at scale.
Why Configuration Drift Matters
1. Silent Security Gaps Most drift doesn’t set off alarms. But each change might weaken your defenses. Over time, this erosion opens the door to:
- Unauthorized access
- Data exposure
- Privilege escalation
2. Failed Audits & Compliance Issues If your settings no longer match policy, your next compliance check could reveal violations you didn’t know existed. Drift is one of the top reasons organizations fall out of alignment with ISO 27001, SOC 2, NIS2, and more.
3. Insider Risk Drift can blur access boundaries. When roles change but settings don’t follow, insider threats become harder to spot.
4. Business Disruption In some cases, drift can even lead to service downtime or data loss—especially when key permissions or integrations are misconfigured.
How to Detect and Manage Drift
1. Monitor Configuration Changes ContinuouslyUse tools that detect configuration changes in real time—not just during quarterly reviews. Look for:
- Admin role updates
- MFA enforcement toggles
- File-sharing permission changes
- Third-party integration changes
2. Track Security Posture Over TimeIt’s not just about knowing what your configuration looks like today—it’s about seeing how it’s changed. Historical baselines are essential to identify drift.
3. Prioritize the Drifts That Matter MostNot every change is critical. Focus on:
- Settings tied to sensitive data
- Admin-level permission shifts
- MFA and access control changes
- Integrations with broad scopes
4. Investigate with ContextA setting changed—but by who? Why? And what impact did it have? Context is everything. Choose tools that correlate changes with user behavior, roles, and app sensitivity.
5. Act on What You FindOnce drift is detected, don’t let it sit. Flag it. Remediate it. Set up workflows that auto-revert risky settings or notify the right owners.
How FrontierZero Helps
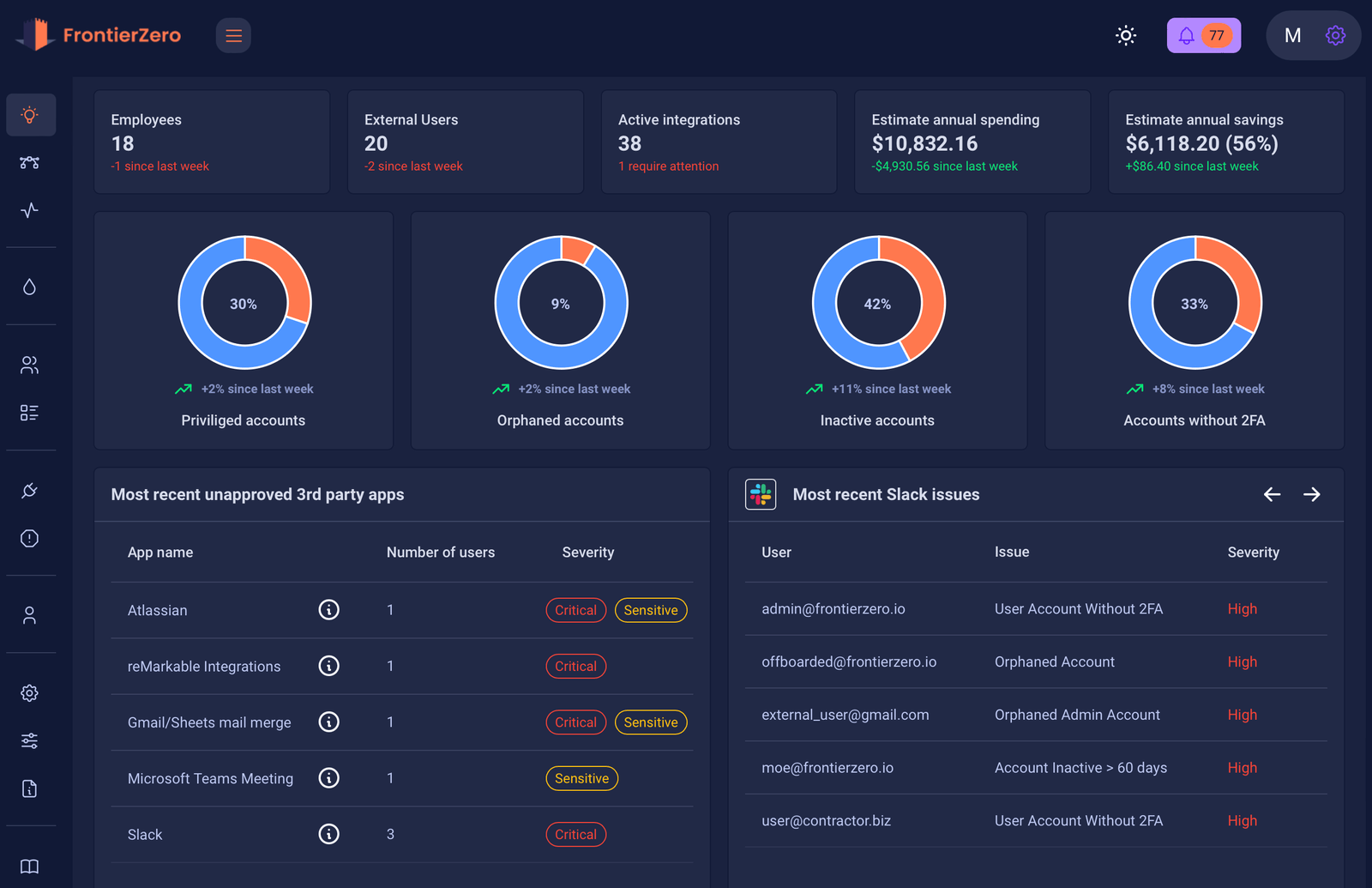
FrontierZero makes drift visible—and manageable.
With our dynamic SaaS posture management platform, you can:
- Continuously monitor security settings across your entire SaaS stack
- See configuration changes as they happen
- Compare current settings against historical baselines
- Flag and prioritize posture drifts by real-world risk
- Automate reporting for compliance and audit readiness
- Investigate changes with full user and business context
No more relying on static snapshots or manual review.
Final Thoughts
In modern SaaS environments, configuration drift is inevitable.
But letting it grow unchecked? That’s optional.
With the right visibility and response, you can turn configuration drift from a hidden threat into a manageable part of your security strategy.
👉 Ready to see what’s changed in your stack? Start your free trial of FrontierZero




