How Can Virtual Browsers Help Reduce the Risk of Phishing?
Phishing attacks are evolving, but virtual browsers offer a secure solution. Discover how this technology safeguards your business from scams.

Table of Contents
- What is Phishing?
- Impact of Phishing
- Zero Day Exploits and Unknown Risks
- What is Sandboxing?
- Virtual Browsers
- Our Virtual Browser Offering
What is Phishing?
Phishing is a type of Social Engineering attacks where the attacker sends a deceptive message to the victim in order to trick them into sharing sensitive information or transferring funds to the attacker. Phishing messages could be sent through Email, SMS or Instant Messaging applications.
Phishing campaigns are usually sent to a large number of people to see who falls for the scam. Meanwhile, Spear Phishing refers to phishing campaigns orchestrated against a specific person or organization. Usually these campaigns are targeted and require some research on the target.
Other types of phishing include:
- Pop-up Phishing: Where a pop-up appears on a website you visit, telling you about a security issue on your computer or a prize that you won along with instructions on who to contact to proceed.
- Vishing: Short for (Voice/VoIP Phishing), which is phishing over the phone. On the other side of that call is someone pretending to be a call center support agent who will ask for personal information or money transfer in various forms.
- Whaling: Phishing that targets senior executives in organizations with the aim of abusing the victim’s privileges in the organizations and causing harm to their companies.
- Watering Hole Phishing: Attackers target a group of users by exploiting a website they’re known to visit and infect the website with an exploit kit which in turn runs the malicious code on the victim’s browser.
Impact of Phishing
A successful phishing attack could lead to a total compromise of the organization. Such compromise could have any of the following ramifications:
- Financial loss: Attackers can either infect corporate systems with Ransomware and ask for a money in exchange for reversing the damage done by the Ransomware or directly trick employees into sending money to attackers, which what happens in Business Email Compromise (BEC) scams.
- Business Disruption: Taking control over privileged accounts and sensitive infrastructure credentials can lead to attackers causing temporary or permanent obstruction to business activities.
- Reputation Damage: If an official channel of communication that belongs to the company is compromised through a phishing attack, it could be used to publish false or misleading information to the public.
Zero Day Exploits and Unknown Risks
While credential theft and phishing scams are the primary goals behind phishing emails, malicious actors sometimes use Exploit Kits to do further damage to the victim.
Exploit kits are tools written by malicious actors with the aim of abusing a security flaw in a web browser, they commonly use what is known as Zero Day exploits. Zero Day exploits are weaponized vulnerabilities found in software but were not yet disclosed to the vendor.
When the victim visits a web page that is hosting an exploit kit using a vulnerable browser or a browser with a vulnerable component, the exploit code runs on the victim’s browser, causing grave damage to the system. In some cases, exploit kits are designed to take total control over the target computer system.
What is Sandboxing?
Sandboxing is a technique in cyber security used to safely run and analyze the behavior of code in environments that emulate or mimic the user’s environment without affecting the user’s actual environment.
Sandboxing is commonly used in malware scanners and Email monitoring, where any files found are executed in safe and isolated environments before flagging the malicious files for the user and preventing their download or execution.
Virtual Browsers
Browsers in themselves are technically considered sandboxes, where all the client-side code received is executed in an isolated environment within the Operating System.
There are many providers that offer Virtual browsers for purposes such as cross-browser QA testing and video streaming. However, it’s not common for them to be used for security testing.
In the security context, Virtual Browsers are used to scan URLs and report any suspicious activity for
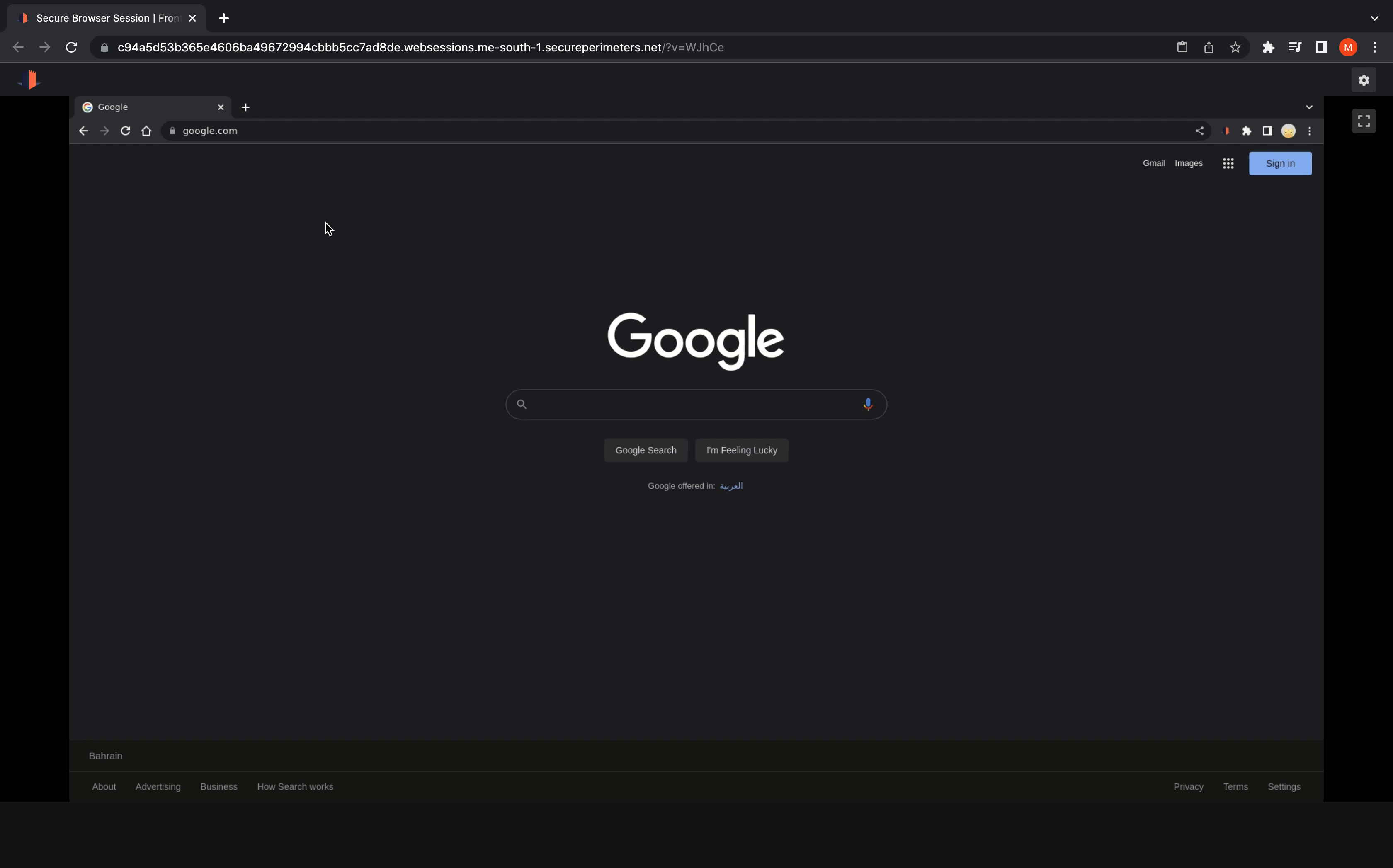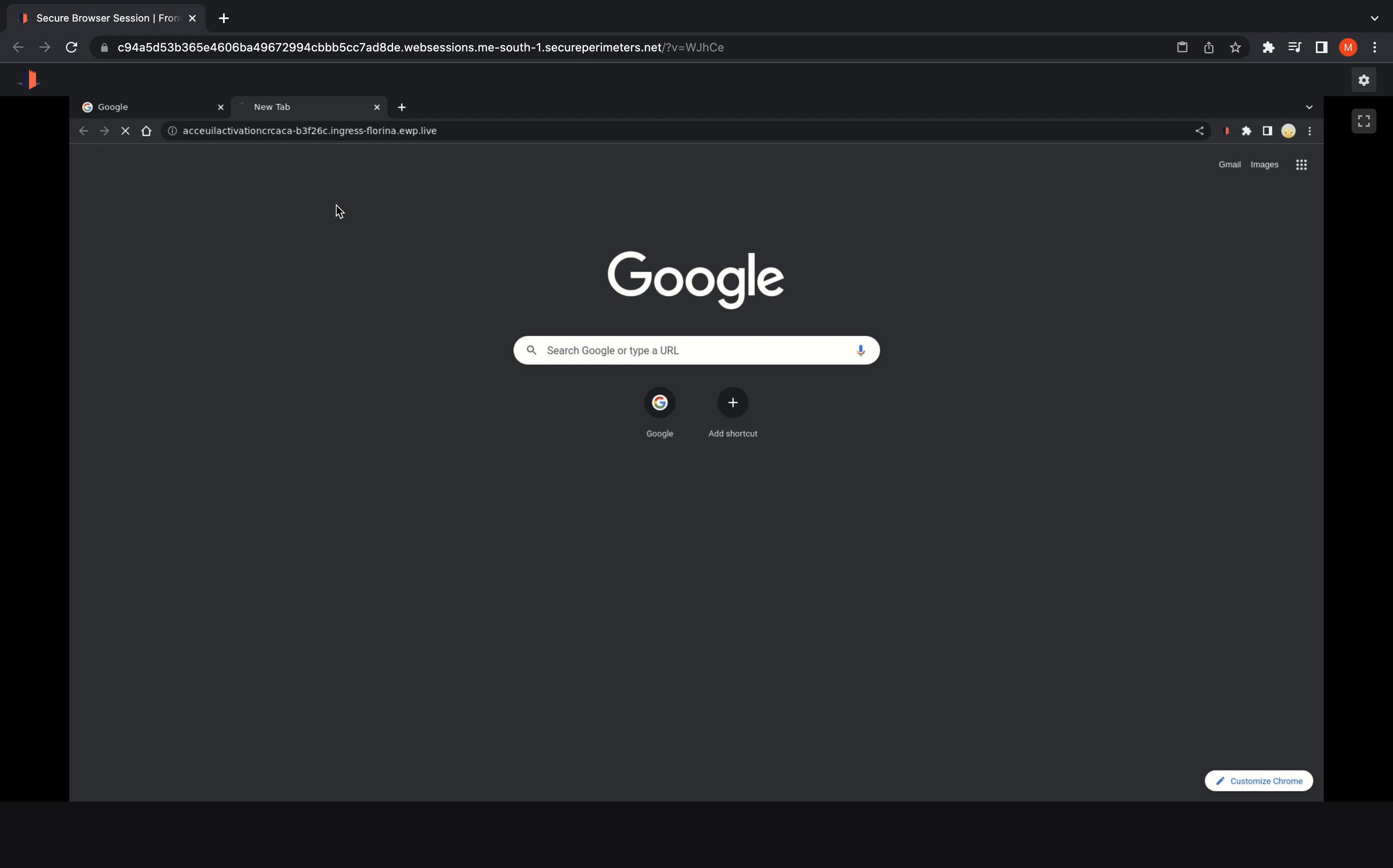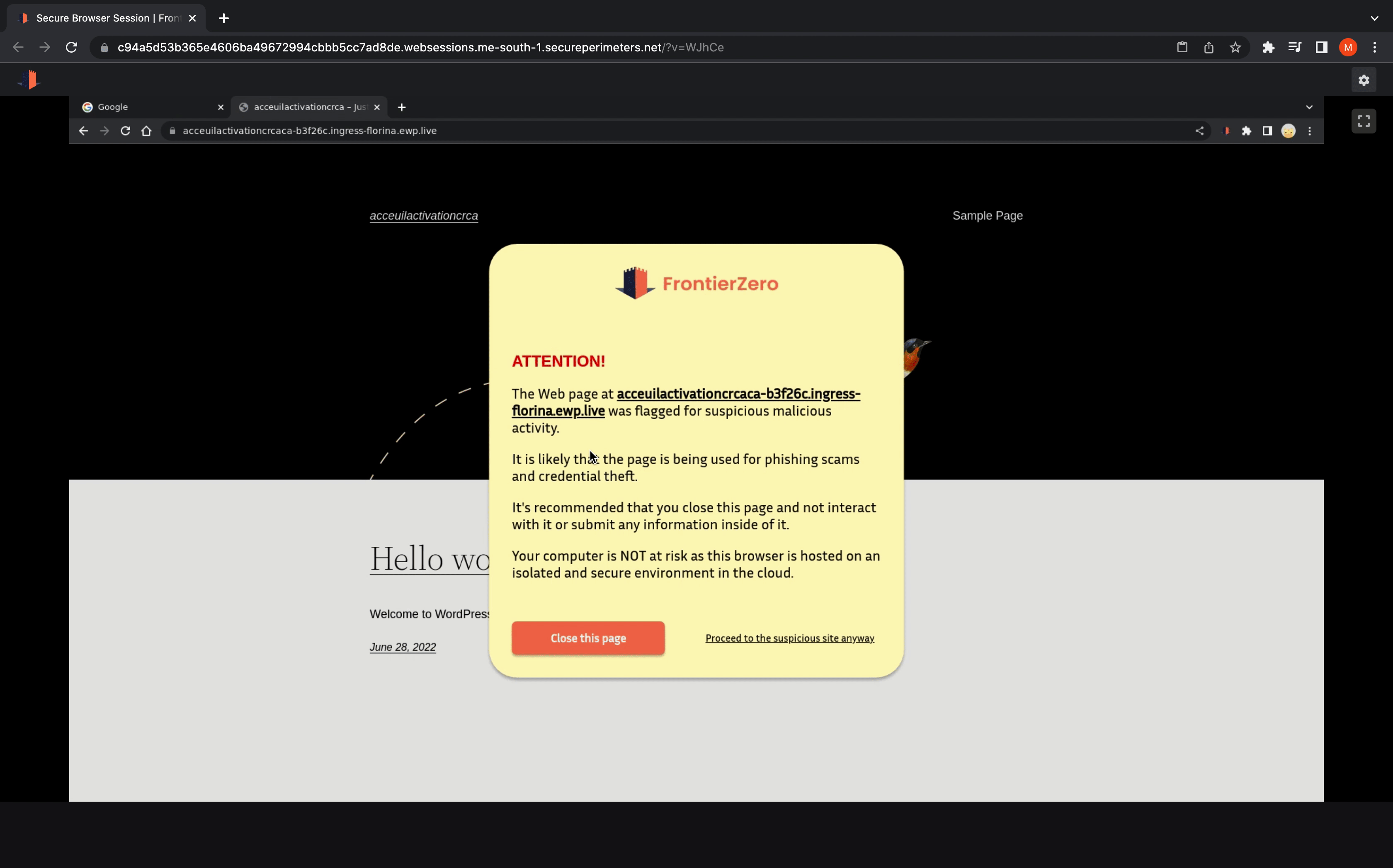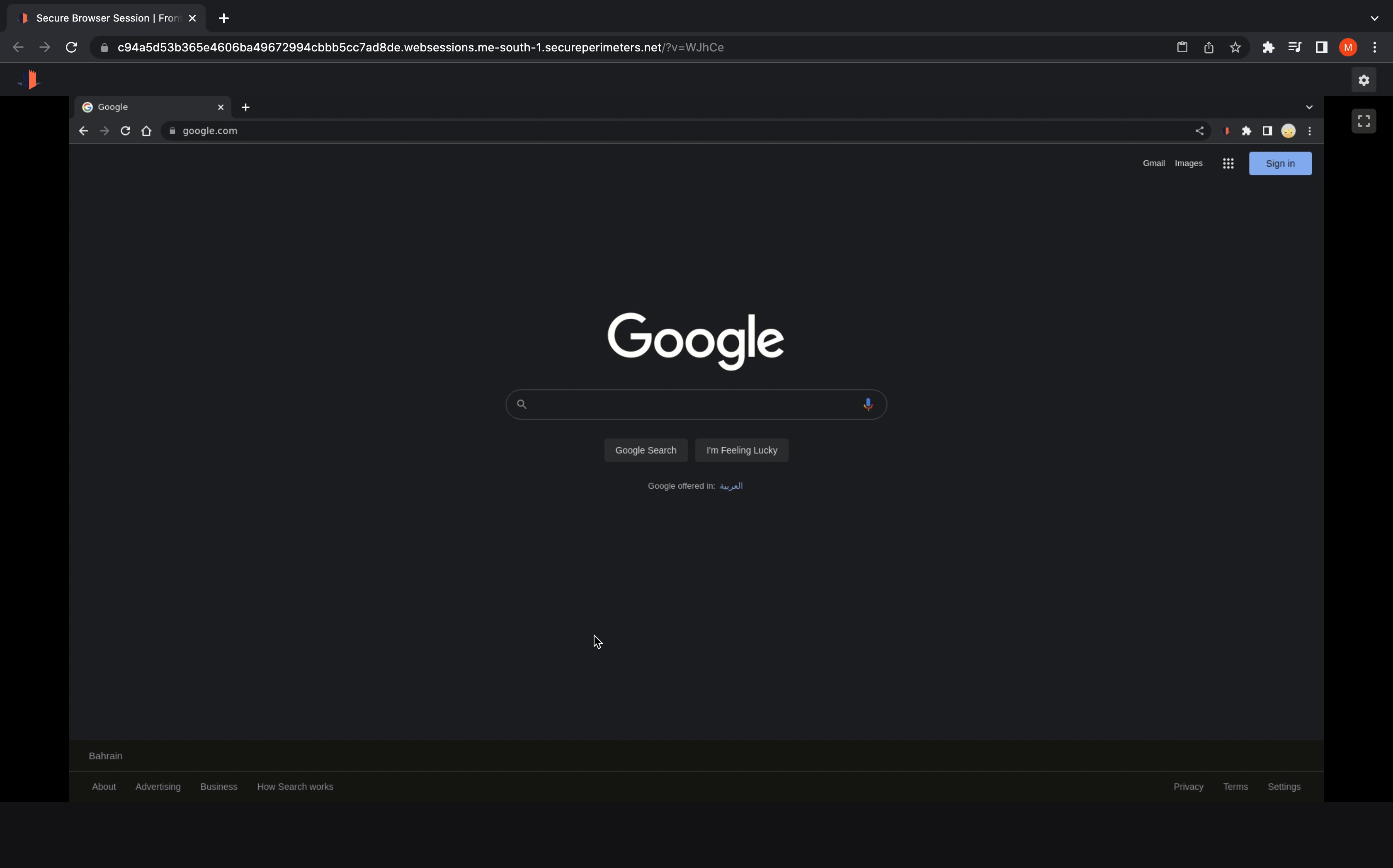
Our Virtual Browser Offering
At FrontierZero, we offer Sandboxed virtual browsers as part of our subscription. Testing URLs in these cloud-based browsers eliminates any risks on the user’s computer.
Furthermore and in order to improve speed and reduce latency, we offer Virtual Browser environments in a number of regions around the world, so users can select which environments are geographically closer to them before running the browser.
To know more information and see this feature in action, book a free demo today




