One Contractor, Global Consequences: How Identity Risk Crippled Jaguar Land Rover
Jaguar Land Rover lost millions when one contractor account went unchecked. This wasn’t a system failure; it was a visibility failure. Here’s what every CISO can learn about identity risk and supply chain trust.

In September 2025, Jaguar Land Rover (JLR), a brand built on engineering precision, went dark.
Production halted across the UK, Slovakia, Brazil, and India. Assembly lines stopped.
Each passing week costs the company nearly £50 million.
The cause wasn’t a zero-day exploit. It wasn’t sophisticated malware. It started with a contractor’s account — a single set of credentials stolen months earlier.
A Breach That Walked Right Through the Front Door
Those credentials had once granted Jira and VPN access. They were never revoked.
When attackers reused them, there was no brute force, no warning, no firewall alert. They just logged in.
From there, more than 350 GB of internal data — including source code, documentation, and employee records — was quietly exfiltrated.
Days later, ransomware swept through JLR’s global infrastructure.
This wasn’t a failure of firewalls or EDR. It was a failure of visibility, of knowing who is logging in, where, when, and why.
How One Identity Became a Global Weakness
The contractor’s access wasn’t privileged. They weren’t an admin. But their account was connected to shared systems, internal apps, and vendor integrations across the supply chain.
Like in most organizations, those connections were trusted by default, but rarely tracked.
A single SaaS login opened the door to internal systems. Internal access spread laterally into production environments.
Each event looked harmless on its own. Together, they brought a global manufacturer to its knees.
Hundreds of alerts appeared across different dashboards. Yet without context, none told the full story.
The Modern Blind Spot
Security leaders face this daily. They can secure employees, devices, and internal networks, but their real exposure lives outside their walls.
Partners. Contractors. SaaS integrations. Each one sits beyond traditional visibility, often with active access long after projects end.
And too many companies still track access through spreadsheets and static dashboards.
So when a supplier’s credentials appear on the dark web, or a vendor logs in from a new region, there’s no real-time signal. No visibility until it’s too late.
But when it happens, the board will ask the same questions:
- Who had access?
- When was it reviewed?
- Why didn’t anyone notice?
And they won't ask them to the suppliers, they will ask them to the company CISO and Security teams.
The Ripple Effect
The JLR breach wasn’t a single IT failure — it was an ecosystem collapse.
- Over 1,000 vehicles per day went unproduced.
- Suppliers lost contracts and laid off staff.
- Dealerships missed deliveries across Europe and India.
- The financial impact exceeded $1.5 billion.
This is a stark reminder that: You’re only as secure as your least secure connection.
What Security Leaders Can Learn
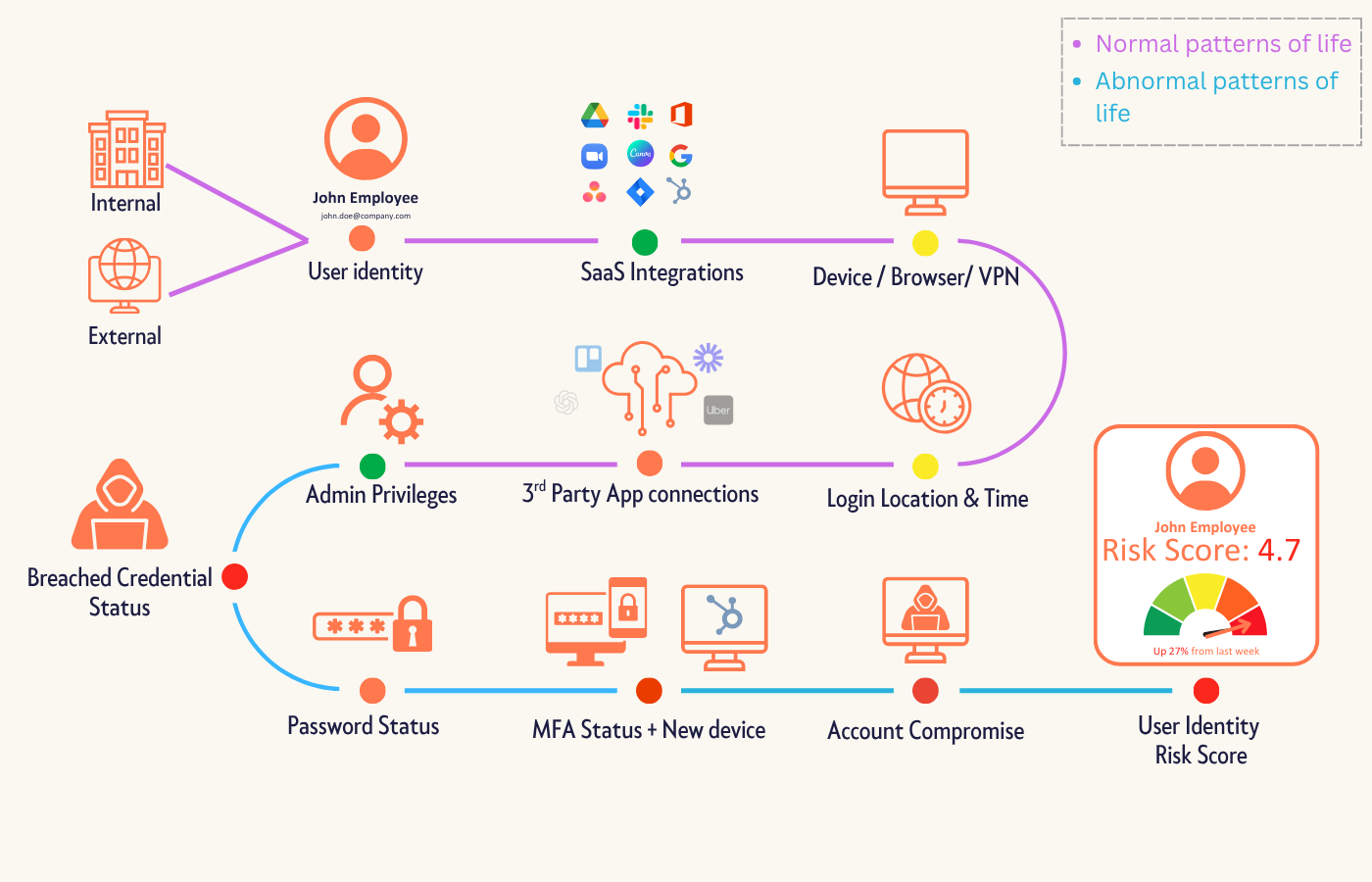
For CISOs, this breach highlights the real-world risks that traditional tools overlook:
- Weak or inconsistent MFA for vendors and contractors
- Old accounts left active after offboarding
- OAuth integrations with unapproved SaaS tools
- Credentials reused across multiple systems
- No behavioral context to separate normal logins from risky ones
- Limited visibility into external connections
What Context Would Have Changed
Now picture this instead: A contractor logs in at 3:27 a.m. from an IP thousands of kilometers away, outside their normal region, without VPN.
FrontierZero instantly correlates this behavior against that identity’s Pattern of Life - the apps they use, when they log in, and from where.
It flags that this account’s credentials were already exposed on the dark web weeks earlier.
Instead of another generic “login anomaly,” security gets a single, contextual alert, the full picture in one view. A response happens in minutes, not weeks.
That’s how context turns noise into clarity.
How FrontierZero Could Have Stopped It
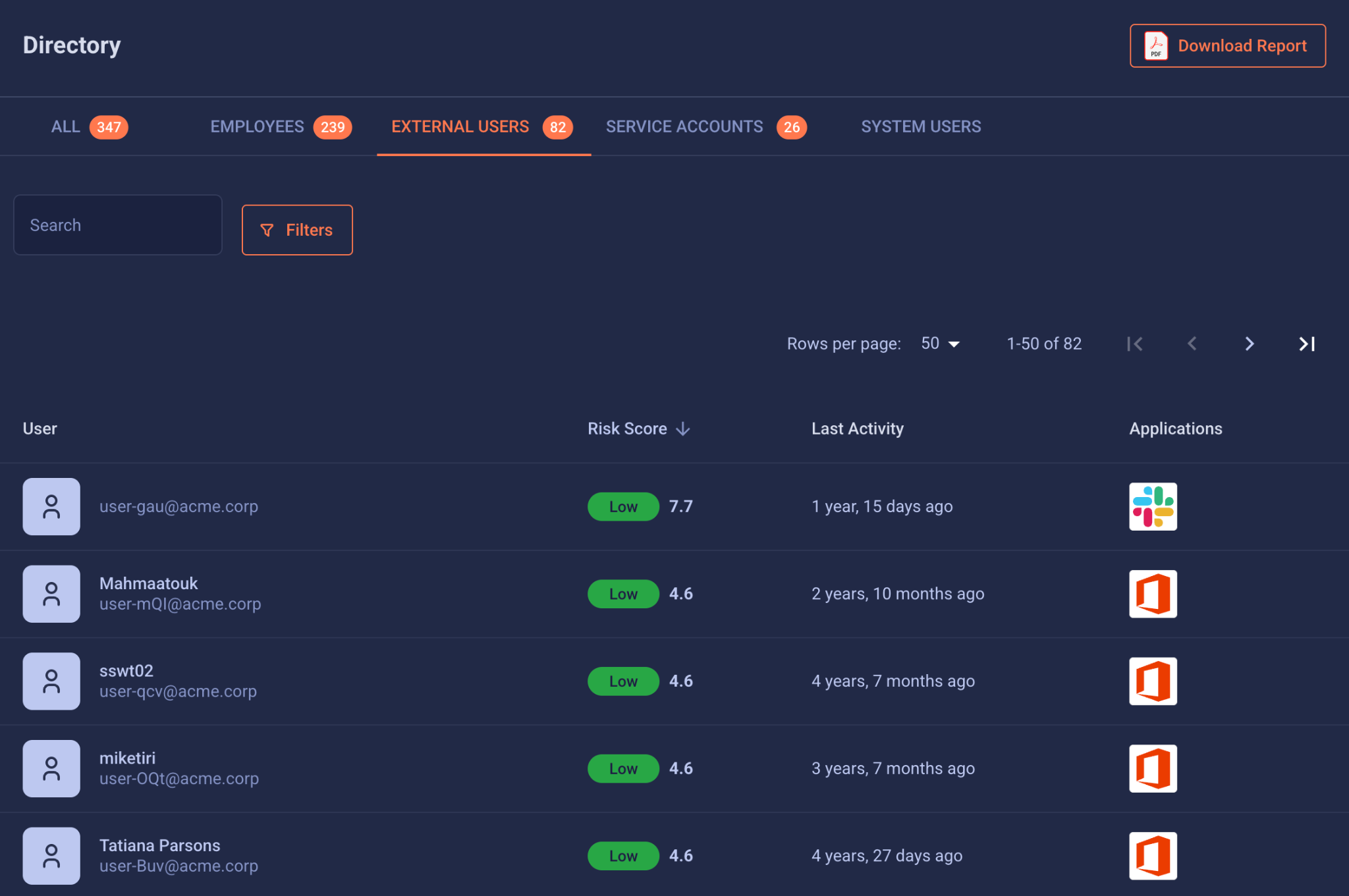
With FrontierZero, those early signs wouldn’t have gone unnoticed:
- Compromised external identity credentials: automatically detected and rotated after dark web exposure.
- MFA visibility: instant insight into enforcement gaps across all SaaS and vendor accounts.
- Abnormal logins: flagged when behavior breaks the usual pattern of life.
- Suspicious downloads: correlated to identity behavior, not just volume.
The difference isn’t another alert — it’s understanding what that alert means.
Why Context Is the Only Perimeter That Still Exists
Every modern organization runs on SaaS. Every SaaS ecosystem runs on trust.
External vendors, remote teams, and integrations make business faster, but also more fragile.
You can’t manage that risk in Excel. You can’t protect what you can’t see. And you can’t trust what you don’t understand.
The companies that avoid the next JLR moment will be those that see connections in context, not as logins, but as living identities.
The Next Step
If your organization depends on SaaS tools and external users, now’s the time to see what’s really happening behind the logins.
🔗 Book a short demo and get a free external connections visibility report. Find the hidden risks before they find you, and get some peace of mind.




