Managing Shadow IT in 2025
Shadow IT has evolved. From AI tools to unmonitored integrations, most SaaS environments have hidden risks. This guide helps you bring them into view.

Why Visibility Into Your SaaS Stack Has Never Been More Critical
By FrontierZero | April 2025
Shadow IT Isn’t Just a Buzzword Anymore
Shadow IT has become one of the most persistent, invisible threats in the enterprise today.
We’re not talking about a rogue spreadsheet or someone testing a new calendar tool.
We’re talking about:
– AI tools connected to corporate data
– SaaS platforms storing sensitive customer information
– App integrations that IT never signed off on
– Teams using apps with no MFA, no monitoring, and no offboarding process
It’s not just a visibility issue—it’s a risk, a compliance gap, and a ticking time bomb.
Why Shadow IT Is So Hard to Contain
In 2025, most companies run hundreds of SaaS apps. Some are managed. Most aren’t.
And with the rise of AI, self-serve tools, and remote work, employees can add apps to your stack in seconds—without ever telling IT.
That’s why the average company now uses:
- 158 SaaS apps per company
- 88 of those are completely unmanaged
- Only 44% of apps are actively governed or monitored
The Hidden Risks of Shadow IT
Shadow IT isn’t just an IT annoyance—it’s a serious business risk.
🚨 Non-Compliance:
Unapproved tools rarely meet regulatory standards like GDPR, DORA, or NIS2. If sensitive data flows through these tools, you’re still responsible.
🔓 Ransomware Entry Points:
Attackers don’t always target your most secure systems. They look for the weak link—often an unmonitored app with poor security settings.
🧨 Lateral Movement:
Once attackers get in, they move laterally—from one app to another. And Shadow IT is the perfect blind spot to hide in.
💸 Budget Waste:
You can’t optimize what you can’t see. Unused or redundant tools silently drain resources—especially when no one’s tracking licenses or logins.
9 Strategies to Manage Shadow IT in 2025
Here’s how leading organizations are tackling the Shadow IT challenge—without shutting down productivity.
1. Discover and Inventory All SaaS Apps
Use modern discovery tools (like identity-based monitoring or API scans) to surface every app in your environment—whether sanctioned or not.
2. Assess and Prioritize Risk
Not every unsanctioned app is dangerous. But some handle PII, customer data, or critical IP. Classify shadow apps by:
- What kind of data they touch
- Whether they support MFA
- Where their data is stored
- How frequently they’re accessed
3. Track Login Behavior Across All Apps
Logins reveal far more than app inventories. By tracking login activity, device type, and location, you can uncover:
- What’s actually in use
- Who’s accessing sensitive tools
- Where policy enforcement is missing
Learn how pattern of life tracking exposes subtle login threats.
4. Apply Policies by Risk Tier
Not every app needs to be banned. Some can be:
- Fully sanctioned
- Monitored only
- Flagged for access review
- Blocked outright Create policy tiers and apply controls accordingly.
5. Balance Productivity with Control
When security gets in the way of work, employees route around it. The solution isn’t blocking—it’s visibility. With better data, you can make smarter trade-offs between flexibility and control.
6. Enforce MFA Beyond Core Platforms
Most companies enforce MFA on Microsoft or Google. But what about:
- Your CRM?
- Your payroll system?
- Your design tools?
If it holds sensitive data, it needs to be protected.
7. Monitor for Misconfigurations and Overexposure
Misconfigured permissions and public file sharing often originate in unsanctioned tools. Regularly audit access controls and file-sharing policies to avoid accidental leaks.
8. Implement Posture Management and Policy Review
Shadow IT risk changes constantly. Use tools that can:
- Continuously assess posture
- Identify gaps in MFA or SSO coverage
- Recommend enforcement actions based on risk
Explore how visibility and Zero Trust go hand in hand.
9. Report to Senior Stakeholders
Your leadership team needs to understand the business impact of shadow IT. Track trends, show risk levels, and align your visibility strategy with broader compliance or financial goals.
Shadow AI: A New Layer of Shadow IT
Shadow AI isn’t theoretical. Employees are already using tools like DeepSeek, Claude, ChatGPT, and others—often copying in sensitive data to generate reports, campaigns, or analysis.
Some of these tools have already been breached. Others are banned in certain countries. Few offer any visibility into how your company’s data is being stored or shared.
Shadow AI is just shadow IT in a new skin—and it needs to be managed the same way: with visibility, policy, and identity-level tracking.
How FrontierZero Helps You Tame Shadow IT
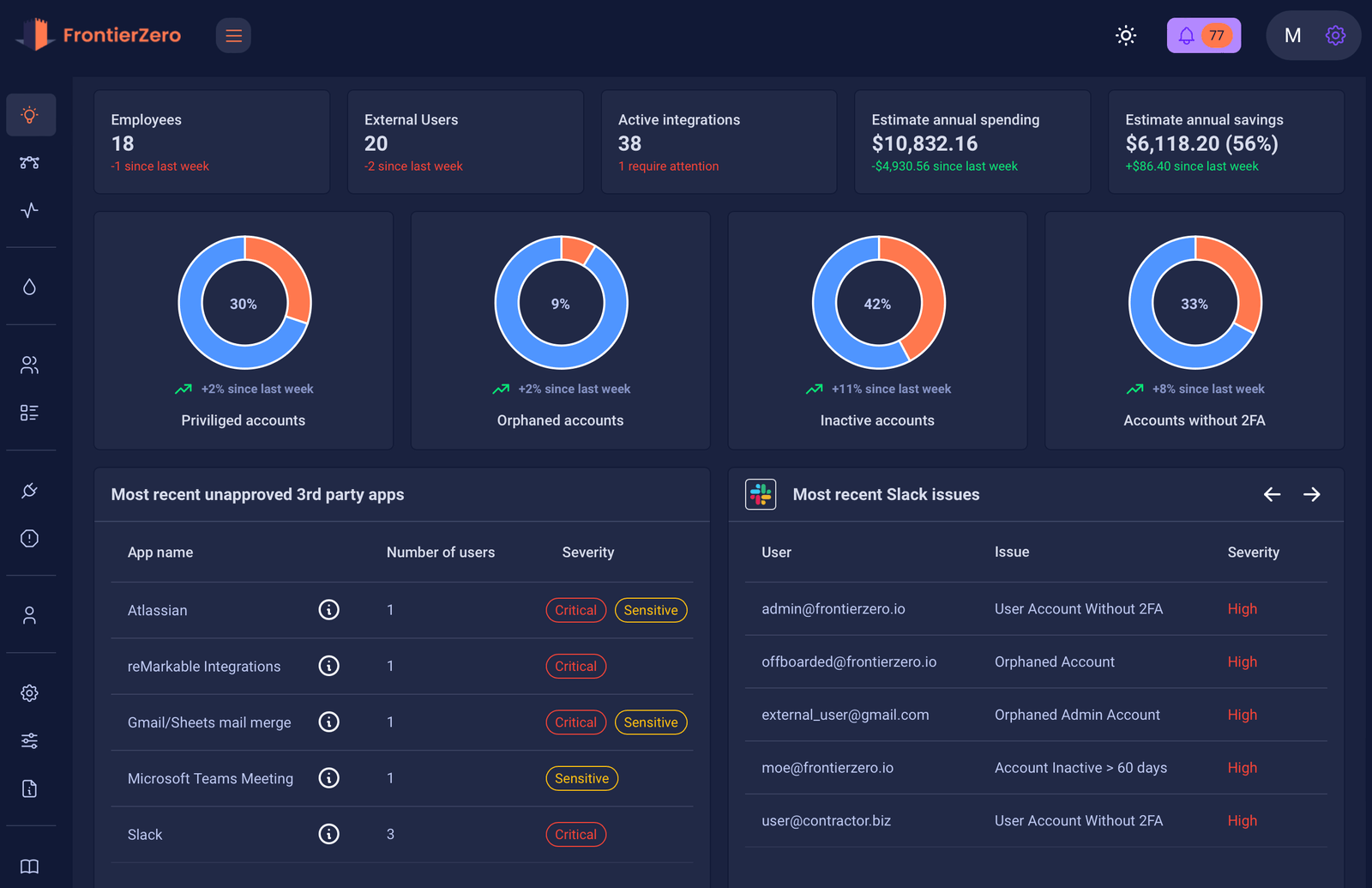
At FrontierZero, we don’t just scan for apps. We give you full visibility into how identities interact with your SaaS stack—even the parts you didn’t know existed.
Here’s what we help you do:
✅ See all apps being accessed by employees—even if they’re unsanctioned
✅ Monitor login behavior, devices, and abnormal activity
✅ Flag tools missing MFA, SSO, or secure configuration
✅ Automatically de-escalate excessive privileges
✅ Audit SaaS usage to improve security and optimize spend
✅ Stay compliant with frameworks like ISO 27001, NIS2, GDPR
Final Thoughts: Shadow IT Isn’t Going Anywhere—But You Can Control It
In 2025, there’s no such thing as a fully locked-down stack.
Employees will always look for faster tools. Departments will adopt new apps to move quicker. Vendors will keep building integrations that fly under the radar.
The answer isn’t to block—it’s to see. To monitor. To know what’s really happening inside your SaaS environment—and respond fast when it changes.
With the right visibility, Shadow IT becomes manageable. Without it? It becomes your next breach.
👉 Want to get full SaaS login visibility in 15 minutes? Start Free Trial Now!
If you are still unsure, here’s why ongoing SaaS monitoring is now a core part of cybersecurity strategy.




