Why Microsoft Security Gives You Confidence, But Not the Full Story
Microsoft gives strong identity visibility, but only inside Microsoft. This explains where today’s SaaS attacks actually start.

Most modern organisations we speak with run on Microsoft.
Identity. Email. Collaboration. Device trust. Microsoft sits at the center of how work gets done.
And because Microsoft gives you such deep visibility inside its own ecosystem, many teams feel they have a clear, reliable picture of what their identities are doing. That confidence is understandable.
But it also creates a quiet assumption: “If nothing looks wrong in Microsoft, nothing is wrong.”
That assumption used to hold. In 2026, it doesn’t.
Because today’s identity doesn’t live inside Microsoft anymore. It moves constantly across SaaS tools, vendors, partners, and external platforms that Microsoft was never designed to see.
This piece isn’t about what Microsoft gets wrong. It’s about what sits outside its line of sight, and why that’s where risk now forms.
Where the visibility naturally stops
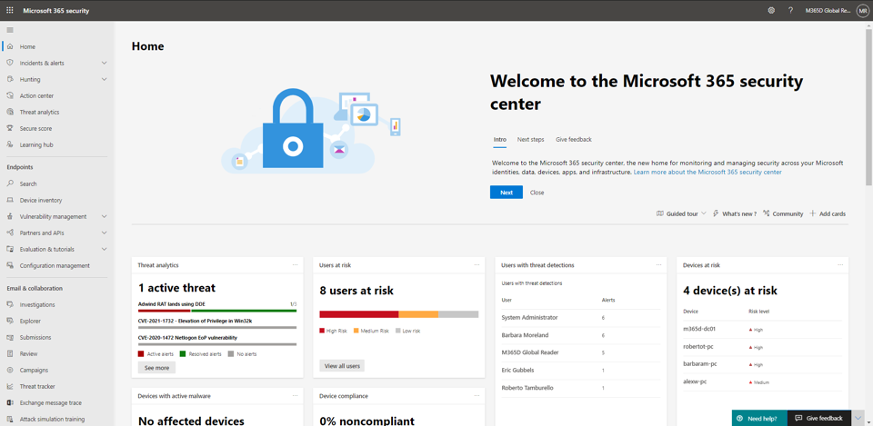
Microsoft gives you deep, high-fidelity telemetry across:
- M365 logins
- Entra ID behaviour
- Conditional Access
- Device trust
- Activity inside the Microsoft suite
For many teams, this becomes their definition of “identity visibility.”But the moment an identity leaves Microsoft, that picture fragments.
- Sales moves into HubSpot or Salesforce.
- Finance uses external billing platforms.
- Marketing works across analytics and ad tools.
- Engineering logs into third-party dashboards.
- Vendors access systems you don’t own.
None of that activity passes through Microsoft.
So even when everything inside M365 looks perfectly normal, the same identity may already be behaving very differently elsewhere, and Microsoft will never show it.
The pattern we keep seeing
A real-world sequence usually looks harmless at first:
09:14 — An employee signs into Microsoft 365 from a known device. Normal location. Normal behaviour. Nothing flagged.
09:37 — The same account logs into HubSpot from a new device
09:38 — Then Salesforce from a different browser
From Microsoft’s perspective, the day is quiet. Inside SaaS, something has already shifted.
Those non-Microsoft logins never appear in Entra. Not because Microsoft failed, but because they’re happening outside its jurisdiction.
This is how early compromise signals slip through: not because security is broken, but because the picture is incomplete.
Why SaaS breaks the old security model
Identity today is not anchored to one platform.
It moves through:
- OAuth permissions that accumulate quietly
- Vendor integrations created automatically
- Shadow tools IT never approved
- External partners logging into shared systems
- Contractors reusing credentials
- SaaS admins operating outside Entra
Attackers follow that sprawl. They don’t try to defeat Microsoft. They step around it.
A normal Microsoft login → followed by unusual SaaS access → followed by odd admin behaviour → followed by subtle data movement
All outside the Microsoft boundary. That’s where modern breaches begin.
Supply chain access makes this even harder
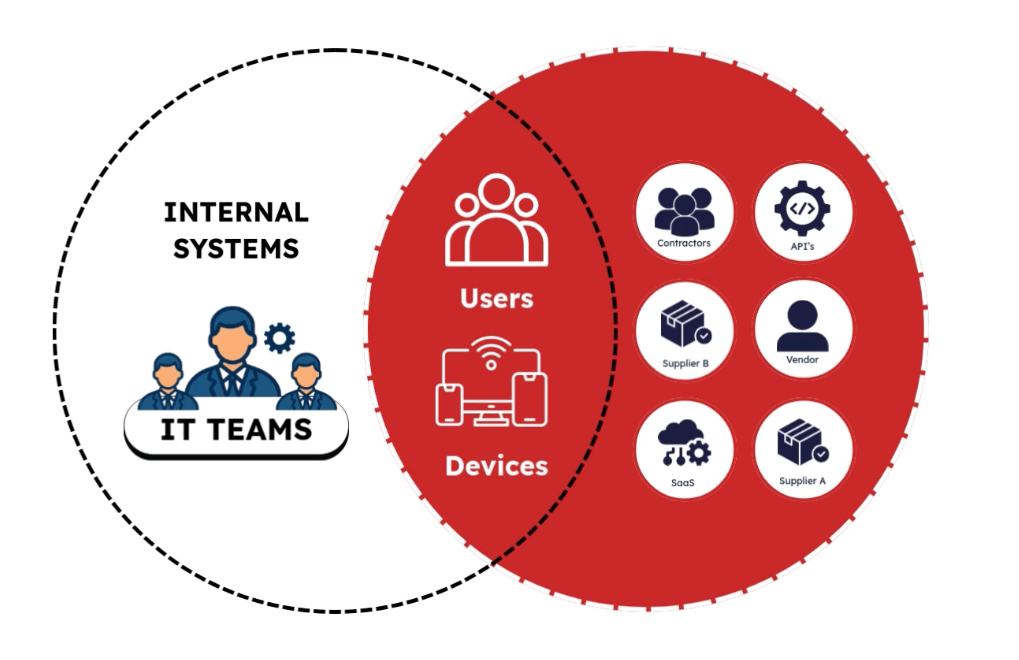
Your riskiest identities are often not your own.
- Suppliers.
- Agencies.
- Service providers.
- Logistics partners.
They get access to SaaS tools that never touch Microsoft at all.
They may reuse passwords.They authenticate from strange locations.They keep permissions long after projects end.
Microsoft shows you what they do in Microsoft. It shows you nothing about what they do across the rest of your SaaS stack.
That isn’t a failure. It’s simply where Microsoft stops.
What mature security teams do differently
The strongest teams aren’t abandoning Microsoft.
They’re adding a second layer of visibility.
- Microsoft for what happens inside Microsoft
- SaaS visibility for what happens everywhere else
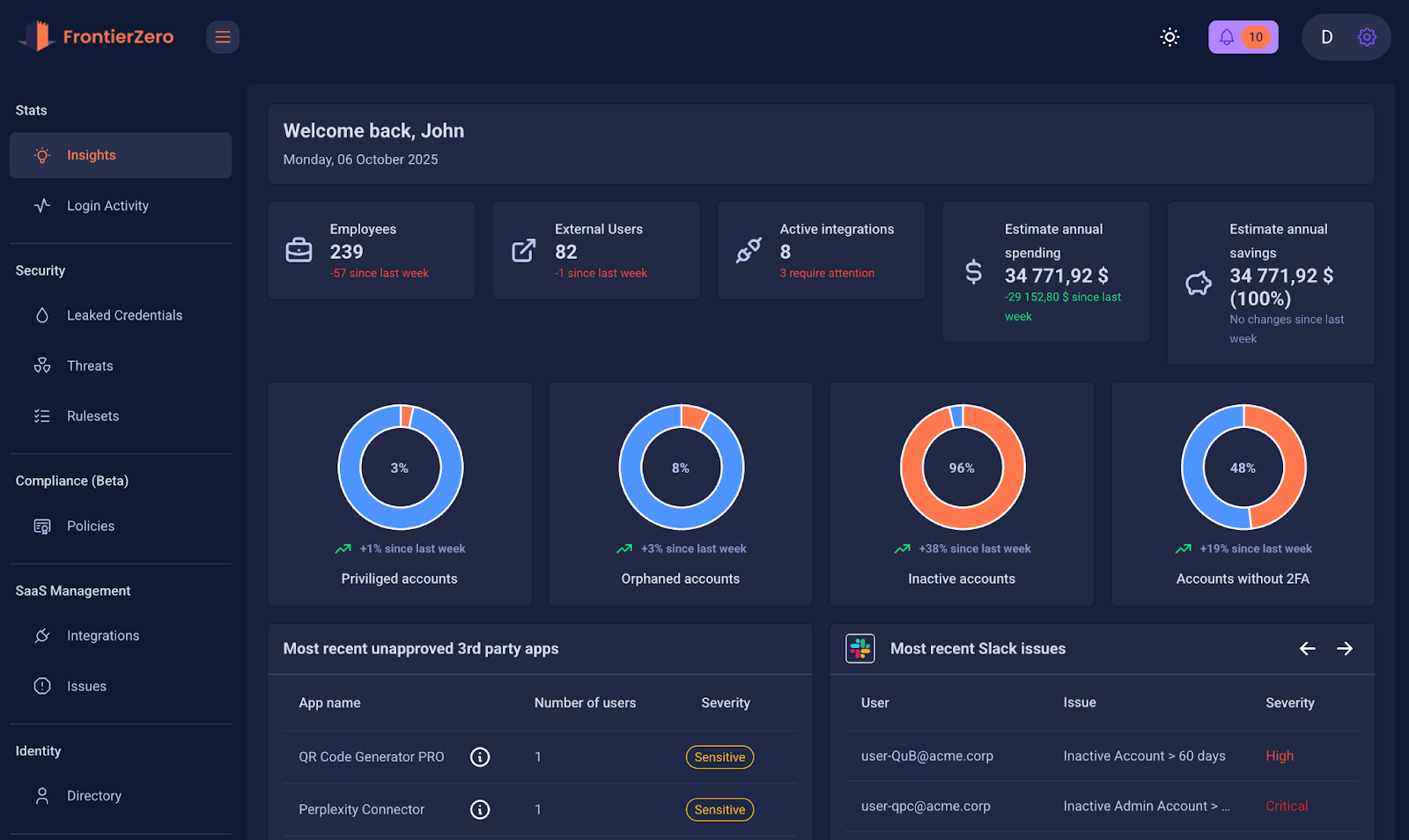
When those layers align, patterns appear that no single platform can reveal:
- External logins that never route through Entra
- OAuth abuse across SaaS apps
- Non-Microsoft admin behaviour
- Vendor identity drift
- Cross-platform session anomalies
- “Normal” M365 accounts behaving very differently elsewhere
Nothing inside Microsoft changes. But the blind spots disappear.
The real question in 2026
Microsoft security is strong. Relying on it for Microsoft visibility makes complete sense.
But the risk today doesn’t live inside Microsoft. It lives between platforms.
So the question CISOs are now asking is not: “Is Microsoft enough?”
It’s: “What is happening to our identities once they leave Microsoft?”
That’s the layer FrontierZero exists to illuminate. Not replacing what you already trust, but making the invisible parts of the identity journey visible before they turn into incidents.
If you want to see what that looks like across your own SaaS and external connections, you can request a short walkthrough.
Because most breaches don’t start where you’re looking. They start just outside it.




