Nissan Data Breach: What Really Happened
In December, Nissan lost customer data — even though its own systems weren’t hacked. The problem came from an external platform with standing access. Read how this happened, why it keeps repeating, and what security teams should change.

In December, Nissan confirmed that 21,000 customers had their personal data exposed.
Not because Nissan’s core systems were hacked. Not because its SOC failed. Not because malware spread inside its network.
But because a third-party platform running on Red Hat was compromised, and that platform had access to Nissan customer data.
If that sounds familiar, it should.
Because this is the same attack path as JLR.
Different vendor. Different breach. Same external-connection failure.

JLR wasn’t an anomaly
It was a pattern
After JLR, many automotive security teams believed:
“We fixed the problem.”
What they actually fixed was one vendor.
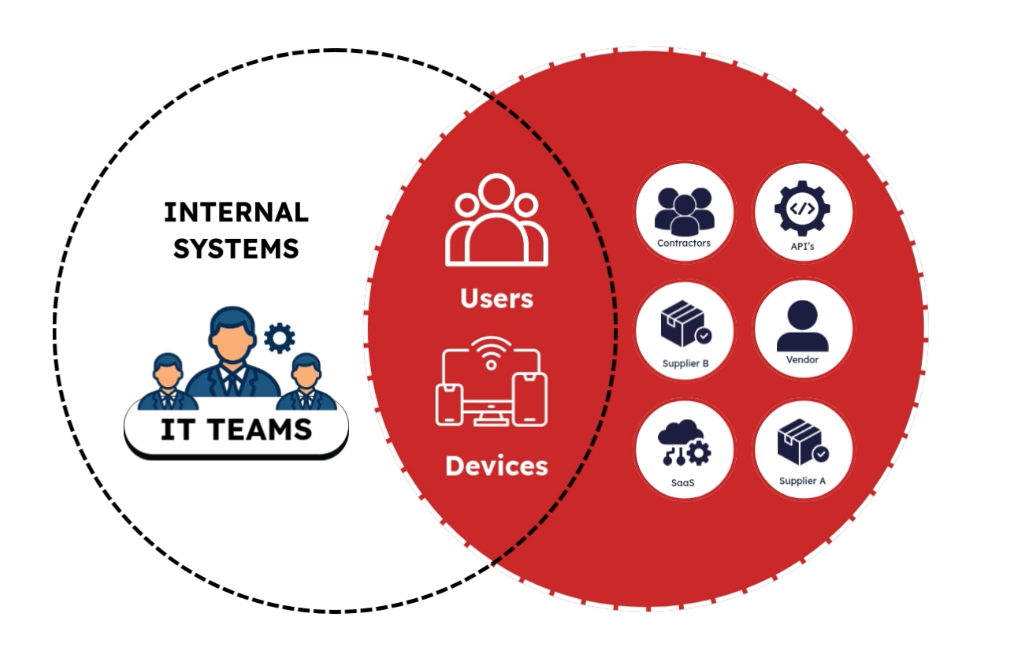
What Nissan just proved is that the attack surface never went away — it simply lives in:
• SaaS platforms
• Vendor environments
• Git repositories
• APIs and service accounts
• OAuth and machine-to-machine access
JLR was compromised through external access. Nissan was exposed through external access.
The perimeter never failed. The connected ecosystem did.

What really happened at Nissan
Nissan’s internal systems were not breached.
Red Hat’s were.
Attackers accessed Red Hat-hosted GitLab infrastructure that contained customer data from companies using those systems — including Nissan’s sales operation in Fukuoka.
That environment:
- Was not owned by Nissan
- Was not monitored by Nissan
- Was not visible to Nissan in real time
So Nissan only learned about the exposure after Red Hat disclosed it.
Not when attackers entered.Not when the data was taken.Not when it was posted online.
After.
That delay is the real risk.
Why does this keep happening
Most automotive security teams can answer:
“What’s happening inside our environment?”
Very few can answer:
“What’s happening inside the environments that have access to us?”
Which vendors currently have OAuth?Which platforms have live API tokens?Which SaaS tools can pull customer data?Which integrations still exist from last year?
JLR didn’t see it.Nissan didn’t see it.
And that’s why attackers never had to touch their networks.
What FrontierZero actually does
FrontierZero wasn’t built to solve one narrow problem.
It was built to solve this one:
You cannot defend what you cannot see.
We map and continuously monitor:
- External SaaS connections
- Vendor integrations
- APIs, tokens, and service accounts
- Vendor and contractor credentials on the dark web
- Data flows across your supply chain
Then we apply the pattern-of-life on top of them.
So when something changes:
- A vendor starts pulling unusual data
- A connection behaves differently
- An integration acts outside its normal pattern
You don’t wait for a breach report.
You see it happen.
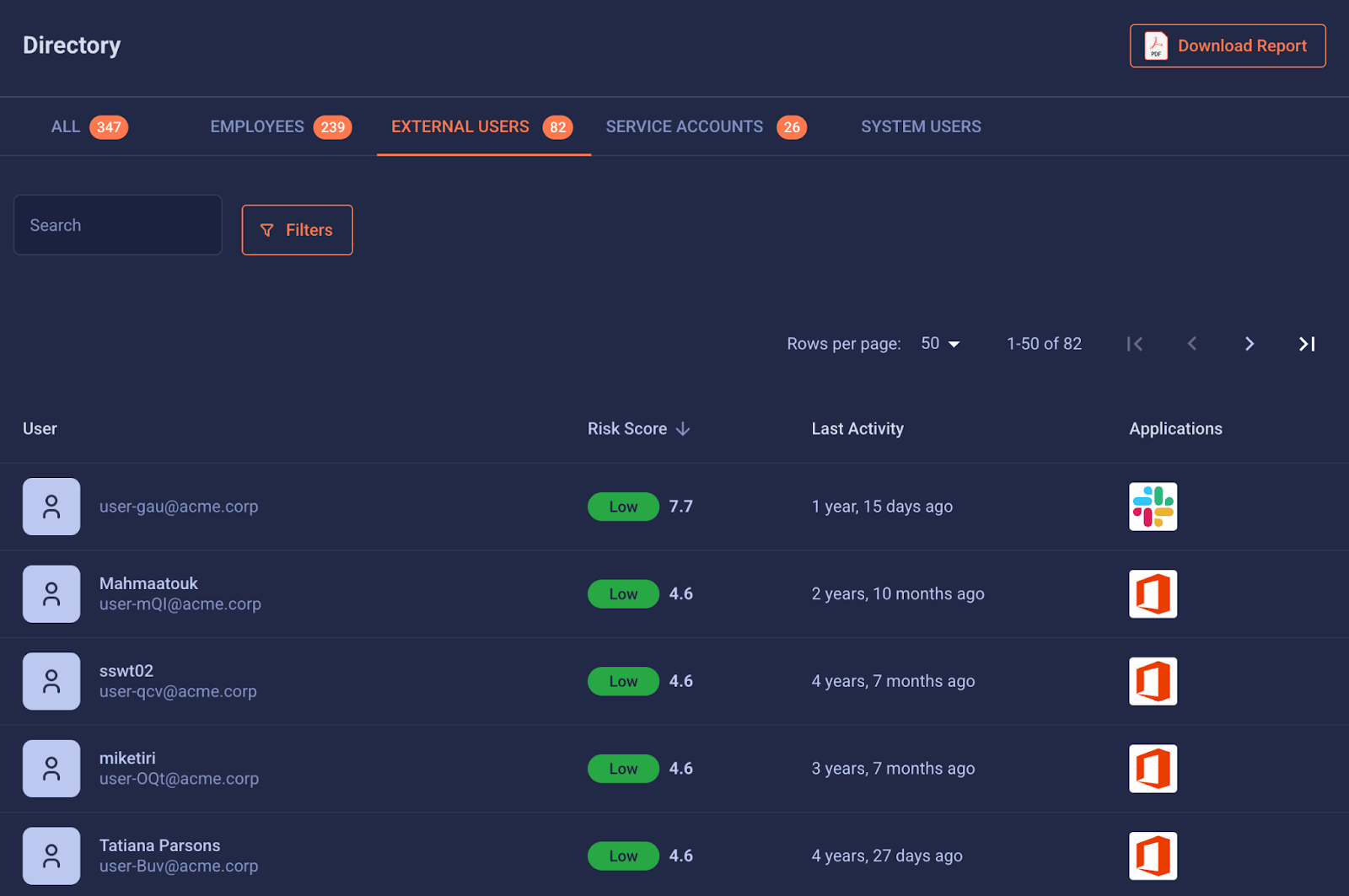
See your own external exposure
We created a 2-minute explainer that shows how external connection security works, and at the bottom, you can request a free external connections report for your environment.
It shows:
- Which third parties have access
- What they’re connected to
- Where your hidden risk actually lives
You can watch it here
Closing thoughts
JLR wasn’t bad luck. Nissan wasn’t a fluke.
They were signals.
Attackers no longer need to break into the company's systems.
They just walk in through those who are connected to the company.
If you don’t have real-time visibility into that ecosystem, you’re already blind to the next breach.




