Privilege Creep: The Hidden Backdoor Hackers Exploit in Your SaaS Environment
Privilege creep happens when users accumulate admin access over time. In SaaS environments, this creates invisible risk: inactive accounts, missing MFA, and external admins hackers love to exploit. Here's how to find and fix it before it’s too late.
Most security teams focus on devices, networks, and endpoints, but attackers don’t care about laptops or servers. They care about users with risky access. And in SaaS-first organizations, that’s exactly where your risk lives.
It’s called privilege creep: when users accumulate permissions over time, often silently, creating doors for attackers. Every lingering access point is a potential entry for a breach, a compliance headache, and a nightmare for IT teams.
Everyday Admin Creep: The Silent Accumulation of Risk
Privilege creep isn’t always dramatic. Often it happens in normal business operations, gradually building risk without anyone noticing:
- The Project Handoff: A developer completes a major feature, moves to a different team, but retains admin access to the original project’s SaaS apps.
- Temporary Promotions: A marketing coordinator covers for a manager on vacation. Elevated permissions are granted and never revoked.
- Cross-Department Access: Finance employees get temporary access to HR or procurement systems during audits, but the permissions linger.
- Vendor & Contractor Accounts: A contractor is granted admin rights for a short project. Months later, their account still exists, forgotten, but active.
- Multiple Tools, Multiple Roles: An employee might have overlapping admin rights across 5–10 SaaS apps due to historical roles or tool migrations. Attackers can leverage a single compromised account to pivot across multiple systems.
These are everyday situations that feel harmless, but together, they create a SaaS security powder keg. Attackers know exactly where to look: accounts with elevated privileges and unmonitored risk signals.
Why Privilege Creep is a Hacker’s Dream
Attackers are no longer smashing firewalls—they’re targeting humans and SaaS accounts. Privilege creep gives them the keys to your most sensitive data:
- Compromised users escalate access
- OAuth apps multiply attack surfaces
- Old or unmonitored accounts linger unnoticed
Scenario: A former contractor still has access to your internal CRM and finance apps. Their credentials are phished in a separate attack. Suddenly, an external hacker can pull customer data, invoices, and confidential projects—all without touching your network.
This is the pain CISOs feel daily: the tools you invest in to protect your network do nothing if the user accounts themselves carry hidden risks.
The Real Cost of Privilege Creep
Unchecked privilege creep doesn’t just create theoretical risk—it causes real financial and reputational damage:
- Data Breaches in SaaS Apps. Attackers pivot through excessive or unmonitored permissions. One compromised account can become a gateway to multiple apps.
- Compliance Violations. Regulators expect strict access controls. Even if permissions are technically correct, unmonitored risk signals like inactive accounts or external admins can trigger audit failures.
- Business Disruption. A hacked high-risk account can delete files, sabotage workflows, or lock out your team. Recovery is expensive and slow.
Example: A SaaS engineer leaves the company but retains access to a critical analytics tool. Hackers compromise the account, modify dashboards, and export sensitive business insights. This can go unnoticed for weeks.
Why Traditional Access Reviews Fail
Manual audits and spreadsheets were never designed for modern SaaS environments:
- Users constantly move between projects, departments, or roles.
- OAuth apps and integrations add invisible permissions.
- Human review is too slow to catch risks before attackers exploit them.
Hackers are fast. They exploit what IT often cannot see.
Actionable Strategies to Stop Privilege Creep
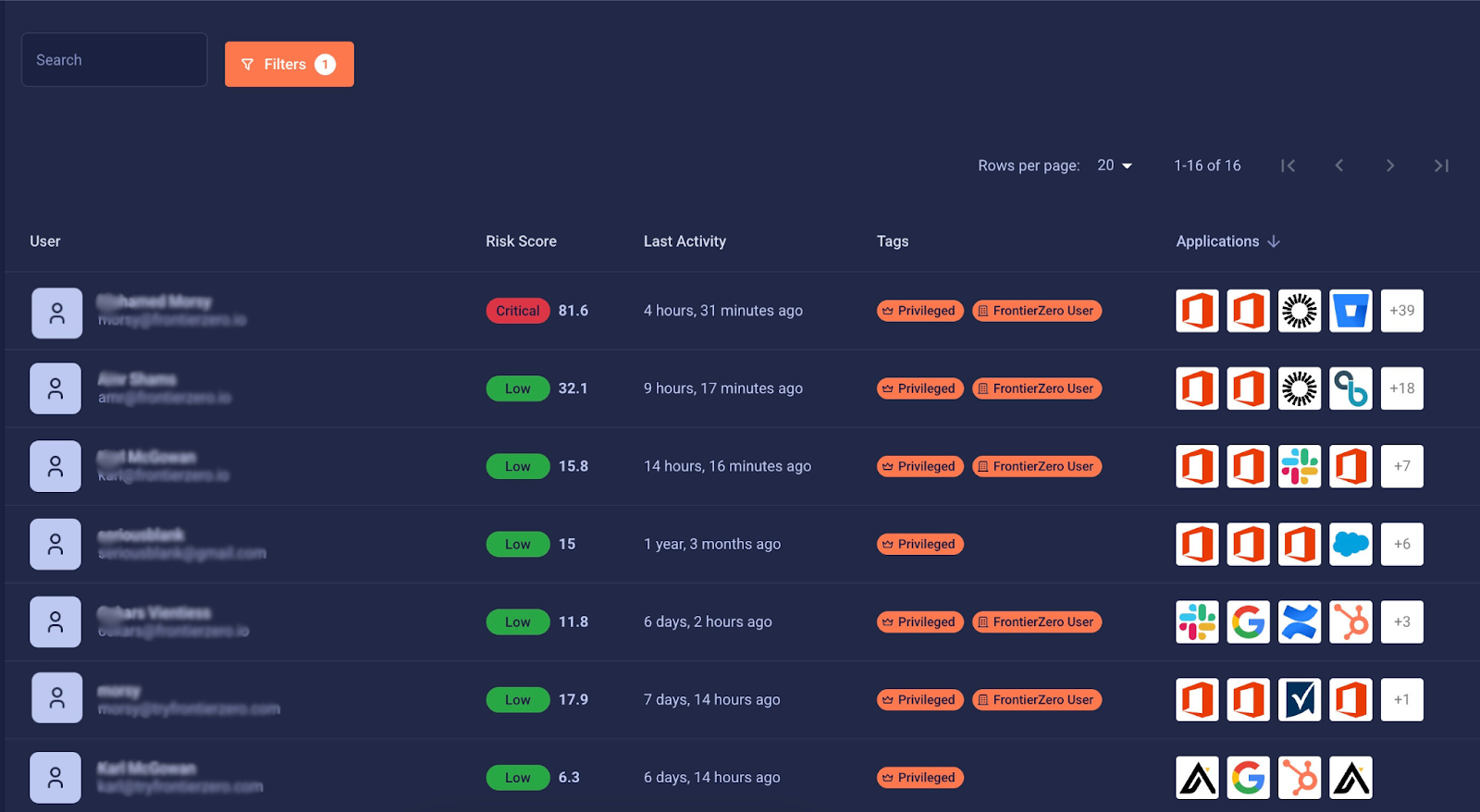
FrontierZero helps CISOs regain control over SaaS access by focusing on identity risk, real-time visibility, and actionable insights:
- Continuous Access Monitoring. Track changes in real-time: new apps, role changes, and OAuth connections.
- Automated Risk Detection FrontierZero flags accounts with high-risk indicators, including:
- Privileged identity status
- External admin access
- Inactive or orphaned accounts
- Missing MFA
- Compromised or breached credentials
- Identity-Based Risk Scoring. Not all elevated accounts are equally dangerous. Prioritize remediation on accounts with the highest risk signals and access to critical SaaS apps.
- Contextual, Actionable Alerts. Understand who has access, why, and what risk they pose. Alerts are clear, prioritized, and enable CISOs to act before attackers exploit the accounts.
The Hard Truth
Privilege creep is invisible, cumulative, and relentlessly exploited by attackers. If your SaaS users have unmonitored risk signals, it’s not a matter of if they’ll be targeted—it’s when.
Every risk signal left unchecked is an open door. Every overlooked account is a potential breach.
FrontierZero helps CISOs see every privileged identity, every risk factor, and every potential attack path—before hackers do.
Ready to close those doors before attackers even knock? Schedule a FrontierZero demo today and see exactly how your SaaS environment can be protected in real time.




