SaaS Shared Responsibility: What Security Leaders Must Know
SaaS providers secure the platform. You’re responsible for everything inside it: users, vendors, permissions, and risk. This blog breaks down where responsibility lies, what’s commonly missed, and how CISOs can prevent the most common SaaS breaches.

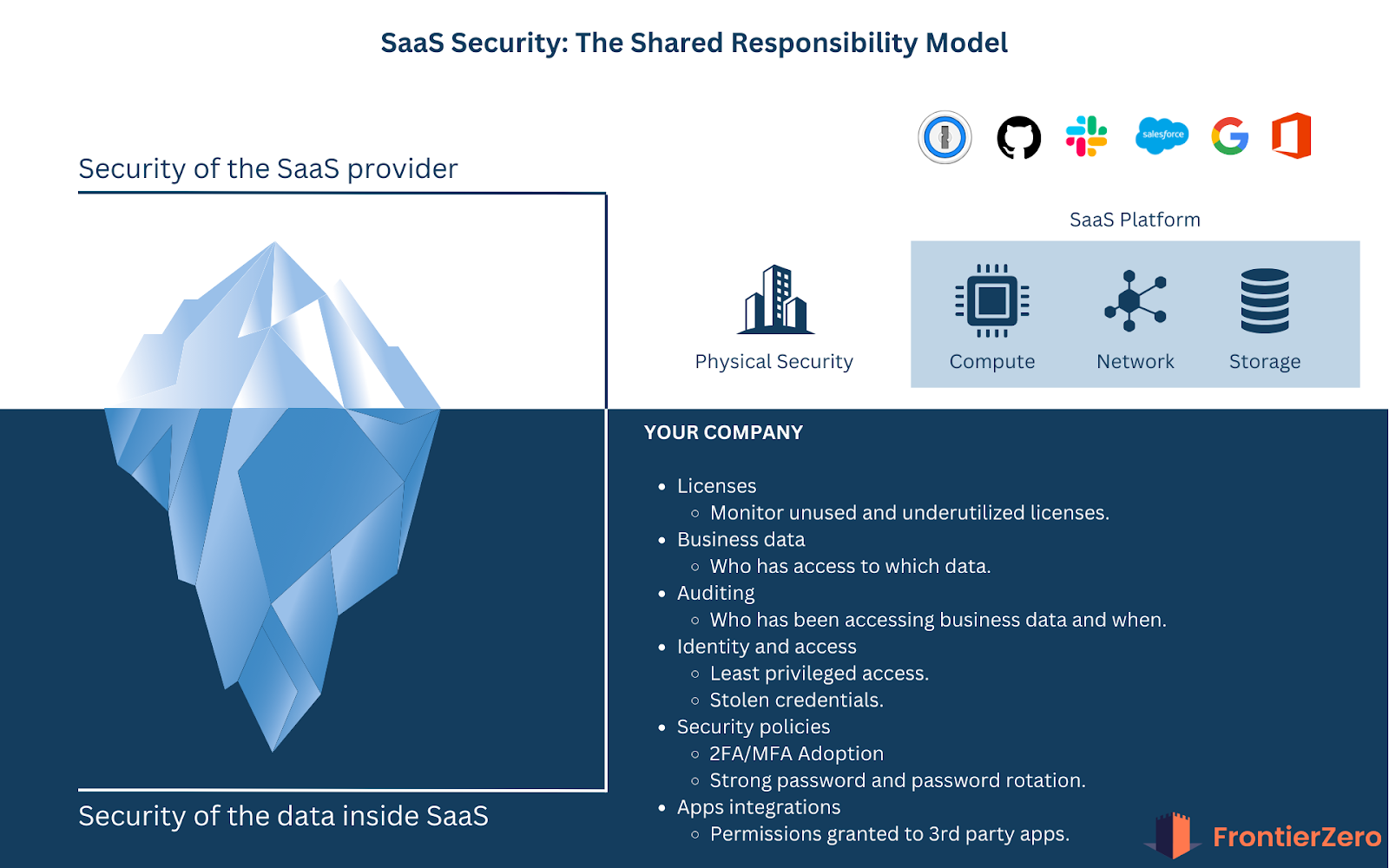
What is Shared Responsibility in SaaS?
SaaS platforms are powerful because they take care of a lot for you — infrastructure, uptime, and platform patches.
But that doesn’t mean everything is covered.
- The provider secures the platform itself: servers, uptime, hardware, bug fixes, and infrastructure-level threats.
- You (the customer) are responsible for how you use it: your data, user access, vendor integrations, configurations, and compliance.
The majority of SaaS-related breaches don’t happen because the provider failed. They happen because of missed responsibilities on the customer side — a misconfigured permission, a vendor with excessive privileges, or MFA turned off on a critical app.
This is exactly what we highlighted in our recent piece on Privilege Creep: The Hidden Backdoor Hackers Exploit in Your SaaS Environment — attackers don’t need a zero-day when over-privileged accounts are already lying in wait.
Why This Matters for Security Teams
For CISOs and IT leaders, the real pain isn’t patching or scanning — it’s the lack of visibility into the parts of SaaS you own.
You’re expected to:
- Prove to auditors that MFA is enforced everywhere.
- Assure leadership that vendors and partners aren’t exposing sensitive data.
- Keep track of who has access across dozens of apps and integrations.
But the reality is:
- Most teams are buried in spreadsheets trying to track accounts and permissions.
- Vendor risk is managed with endless questionnaires that are outdated as soon as they’re filled in.
- Oversight is split across 20+ dashboards, each showing a fragment of the picture.
And yet, when something goes wrong — you are the one held accountable.
That’s the tension of shared responsibility: the provider keeps the lights on, but you’re expected to see every user, every connection, every risky change — even when the tools make it nearly impossible.
We’ve seen how this plays out in practice with shadow IT. In our research on The Top 5 Departments Most Likely to Use Shadow IT, marketing and finance consistently emerged as hotspots for unapproved SaaS apps. Every one of those apps increases your responsibilities — and your blind spots.
Key Domains of Shared Responsibility
Understanding where your job starts (and where the provider’s ends) is critical. Here’s how the lines are drawn:
What Happens When Shared Responsibility Fails
Neglecting customer responsibilities leads to predictable and expensive problems:
- Unauthorized access through vendor integrations that nobody is monitoring.
- Data leakage from overly broad or misconfigured permissions.
- Insurance denial when policy requirements (like MFA) aren’t consistently met.
- Leadership fallout when breaches escalate into public headlines and boardroom accountability.
IBM’s Cost of a Data Breach Report 2025 put hard numbers on this: third-party compromises averaged nearly USD 5M per incident in the Middle East, where breach lifecycles regularly exceed 250 days. We broke down the broader findings for CISOs in our Top 5 Takeaways from the IBM Cost of a Data Breach Report.
The lesson is the same: these aren’t “provider failures.” They’re customer-side gaps — and they’re expensive.
What CISOs and IT Leaders Can Do
Owning your side of the model means treating SaaS risk as a continuous process, not a quarterly checkbox.
Practical steps include:
- Visibility first: Map every app, user, integration, and permission in real time — not “as of last quarter.”
- Enforce controls: Make sure MFA, role management, and access removal are consistent across all apps.
- Vendor vigilance: Review vendor access regularly, update contracts, and cut off integrations when they’re no longer needed.
- Demand proof: Be ready to show at any moment that controls were active before an audit or breach.
The Bottom Line
SaaS providers secure the platform. You secure everything inside it.
If you’re still treating shared responsibility as “an IT checklist,” you’re already behind.If you treat it as a live, continuous responsibility — supported by visibility into users, vendors, and integrations — you’ll avoid surprises, insurance denials, and boardroom fallout.
Because in 2025, shared responsibility isn’t about who patches the servers. It’s about who sees the risk before it costs millions.




