Top 5 Reasons to Monitor Your SaaS Apps in 2025
With SaaS tools driving modern business operations, unmonitored apps can become a major risk. In 2025, learn how to mitigate threats from AI, ex-employees, shadow IT, and misconfigurations while improving your security posture with proactive monitoring.

SaaS applications are the backbone of modern business operations, enabling teams to collaborate, innovate, and stay productive. However, as the reliance on SaaS tools grows, so do the risks associated with unmonitored access, data sharing, and security gaps.
In 2025, with emerging technologies like AI, evolving cybersecurity threats, and stricter compliance requirements, monitoring your SaaS ecosystem isn’t just recommended—it’s essential. Let’s explore the top five reasons why proactive monitoring should be a priority this year.
1. AI Tools: Are They Protecting or Exposing Your Data?
AI-powered tools are transforming the workplace, from generating reports to managing schedules and analyzing data. While they enhance productivity, their access to critical business data poses significant security risks.
For example, an AI writing assistant integrated with your SaaS apps might request access to your company’s cloud storage to “learn” from past documents. While convenient, this opens the door to unintended data exposure if the AI tool is compromised or if employees input sensitive information into prompts.
In 2025, as AI adoption surges, businesses must monitor:
- Permissions: What data AI tools can access and how it’s being used.
- Employee Behavior: Ensuring sensitive information isn’t inadvertently shared with AI platforms.
Regular SaaS monitoring ensures AI tools are used responsibly, protecting your company from unintentional data leaks.
2. Ex-Employees: Silent Risks Lurking in Your Systems

One of the most persistent security challenges is managing access for employees who leave the organization. Studies show that 89% of ex-employees retain access to at least one SaaS application after their departure.
Consider a scenario where a former employee still has access to your CRM. Without proper monitoring, they could view sensitive client data, download reports, or worse—use the access for malicious purposes.
To mitigate this risk, SaaS monitoring should focus on:
- Automated Access Revocation: Ensuring accounts are deactivated immediately upon offboarding.
- Regular Audits: Reviewing user access to identify dormant or unauthorized accounts.
Proactive monitoring closes these gaps, reducing insider threats and protecting your business from preventable security breaches.
3. Shadow IT: The Unseen Security Gap

Shadow IT—the use of unauthorized SaaS applications within an organization—will continue to rise in 2025. With an estimated 40% of IT spending occurring outside the control of IT departments, many tools remain unmanaged and unmonitored.
These shadow apps often house critical business data or connect to your authorized SaaS platforms, creating security vulnerabilities. For example, a marketing team might integrate an unapproved analytics tool with your CRM, inadvertently exposing sensitive customer data through insecure connections.
SaaS monitoring helps:
- Detect Unapproved Apps: Identifying unauthorized tools in your environment.
- Assess Risks: Evaluating data access permissions and integration vulnerabilities.
By monitoring for shadow IT, organizations can enforce security policies and ensure all SaaS tools are accounted for.
4. Two-Factor Authentication (2FA): A Simple Step with Big Impact
In 2025, cybersecurity threats are more sophisticated than ever, with phishing attacks and credential theft continuing to target SaaS environments. Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) remains one of the most effective defenses against unauthorized access.
However, many organizations still fail to enforce 2FA across all their SaaS applications. This oversight leaves sensitive data vulnerable to breaches, particularly if passwords are compromised.
Monitoring your SaaS ecosystem ensures:
- 2FA/MFA Enforcement: Identifying accounts where 2FA is not enabled.
- Compliance: Meeting regulatory requirements for strong authentication practices.
By actively monitoring 2FA settings, businesses can significantly reduce the risk of costly breaches while maintaining compliance with industry standards.
5. Misconfigurations: The Overlooked Security Threat

In 2025, misconfigurations are a leading cause of SaaS-related security incidents. A single error—such as leaving a cloud storage folder public or failing to restrict administrative permissions—can expose sensitive data to unauthorized users.
Recent examples show how devastating misconfigurations can be, with breaches caused by exposed cloud buckets or mismanaged user permissions leading to millions in fines and lost revenue.
Effective SaaS monitoring can:
- Identify Misconfigurations: Highlighting open access, excessive permissions, or improperly secured integrations.
- Enforce the Principle of Least Privilege: Ensuring users only have access to the data and tools they need.
- Protect Sensitive Data: Regularly reviewing app settings to catch vulnerabilities before they’re exploited.
With proper monitoring, organizations can catch and correct these errors, strengthening their overall security posture.
How Monitoring Protects Your SaaS Ecosystem
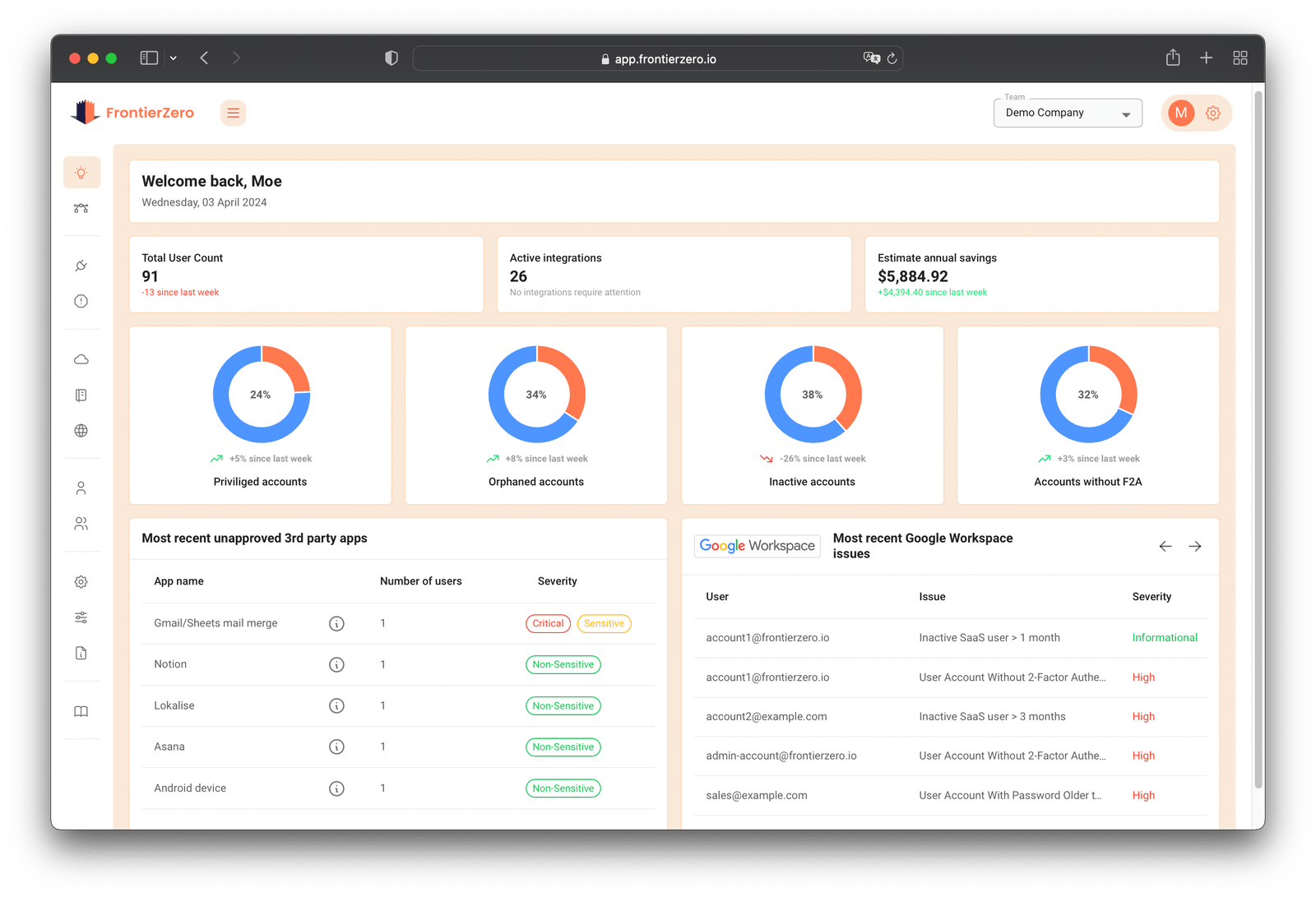
Proactively monitoring your SaaS applications is no longer optional—it’s a business necessity. By addressing risks from AI tools, ex-employees, shadow IT, security misconfigurations, and weak 2FA enforcement, you can:
- Protect sensitive company data from breaches and leaks.
- Reduce unnecessary costs by identifying unused or unauthorized apps.
- Ensure compliance with evolving security and regulatory standards.
Take Control of Your SaaS Security
In 2025, FrontierZero empowers organizations with the tools they need to monitor and manage their SaaS environments effortlessly. With FrontierZero, you can:
- Gain full visibility into SaaS usage and access.
- Detect and resolve security risks like misconfigurations or shadow IT.
- Automate critical processes, from offboarding to enforcing 2FA.
Ready to secure your SaaS ecosystem? Start your free trial today and experience the benefits of complete visibility and control with FrontierZero.




