What Is Context-Based Security (and Why the Old Way Doesn’t Work Anymore)
Most breaches slip through not for lack of alerts, but for lack of context. Context-based security brings clarity to chaos — helping teams focus on what’s real.

For years, security was about checking boxes.
MFA? ✅
Password rotation? ✅
Device management? ✅
But even with every box ticked, breaches kept happening. Because security teams were making binary decisions: “allow or deny”, without truly understanding the context behind each login.
The truth is: a login alone tells you almost nothing. It tells you who entered their credentials. It doesn’t tell you how, when, where, or why.
And that’s the difference between traditional identity-based access and context-based security.
Identity tells you who the user is. Context tells you whether the situation makes sense.
The Problem With Old Solutions
Legacy authentication models were designed for a simpler world. A world where users sat inside a trusted network, behind a firewall, logging into a few corporate systems.
Today, users connect from airports, coffee shops, and home offices across dozens of SaaS platforms that IT didn’t even approve.
Credentials leak on the dark web, MFA fatigue becomes the new phishing, and unmanaged devices quietly slip into your environment.
Old solutions can’t adapt to that chaos because they don’t look beyond the login prompt. They assume:
- If credentials match → allow access.
- If MFA passes → trust user.
That binary model ignores the reality that risk changes every second, depending on what’s happening around the user.
Context Is the New Security Perimeter
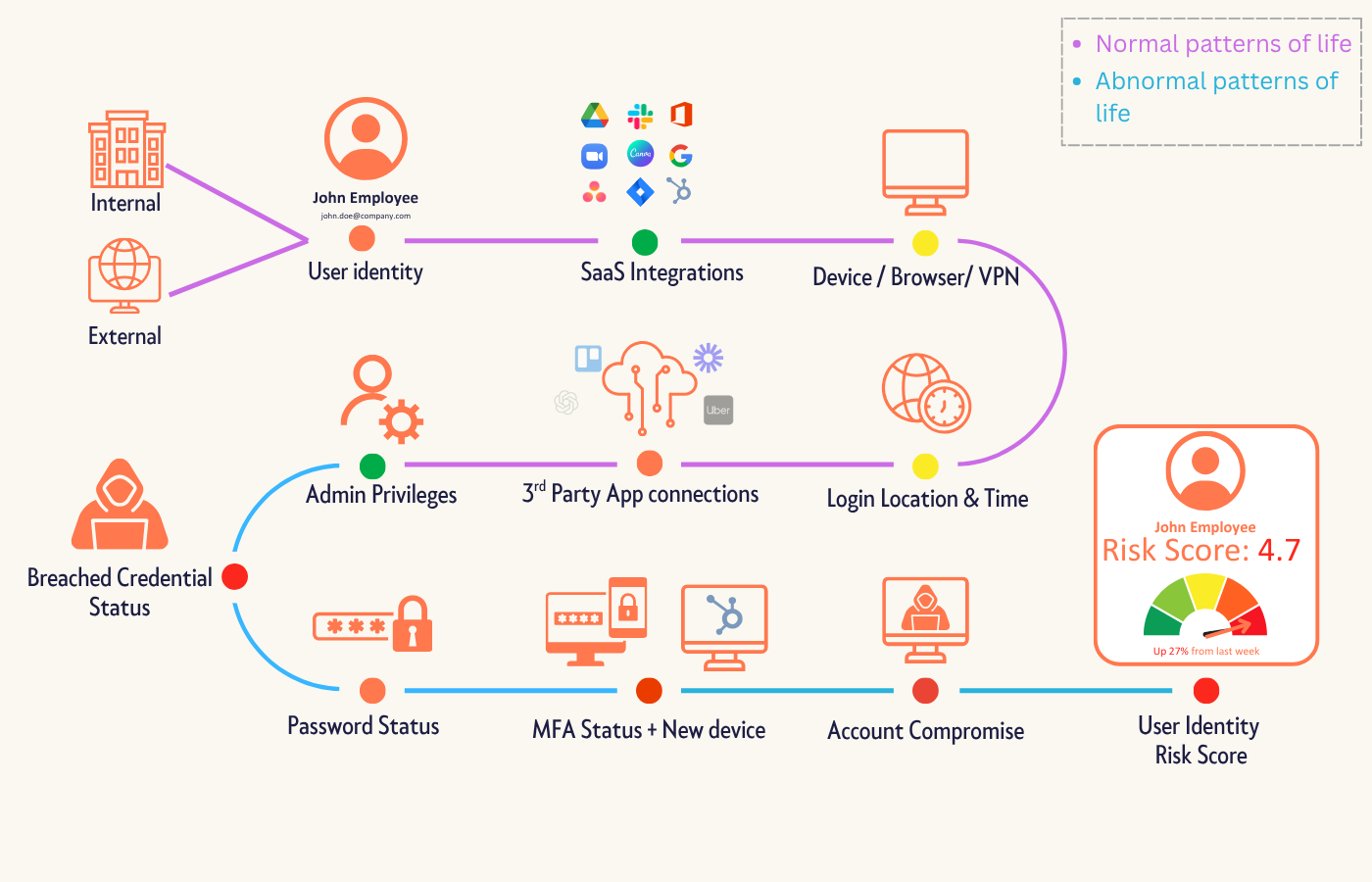
Context-based security means access is granted dynamically, based on behaviour, environment, and intent. It asks:
- Does this login match the user’s typical pattern of life?
- Is the device managed, healthy, and compliant?
- Is the location familiar or unusual?
- Is this action high-risk given their role?
When the context doesn’t make sense, access can be challenged or denied. When it aligns with normal behaviour, access stays smooth and invisible.
This is what we call the pattern of life: the continuous rhythm of how users normally work across your SaaS ecosystem. Once you understand that rhythm, any deviation becomes a signal worth investigating.
Three Logins, Three Different Risks
Let’s make it real. Here are three simple login attempts, identical at first glance. But when viewed through context, they tell completely different stories.
Scenario 1: The CFO
A 2:37 a.m. login attempt. From a Windows device. No MFA enabled .Location: foreign country.Password? Recently found on a dark web dump.
On paper, it’s just another credentialed login. But in context, it’s a flashing red flag.
That combination of timing, location, device, and credential risk should trigger immediate containment. Context doesn’t just identify risk; it quantifies it.
In this case, everything aligns with a potential account takeover attempt.
Block. Investigate. Escalate.
Scenario 2: The Sales Manager
Another 3 a.m. login attempt.Also from abroad. No MFA, but on a managed device and through a VPN.
Risky? Yes. Malicious? Maybe not.
Context tells us this user often travels, and the VPN IP matches a corporate range. While the timing is odd, the rest of the picture suggests this could be a legitimate remote login.
Instead of a full block, context can trigger a step-up verification, a quick re-authentication before granting access. Friction only where it matters.
Scenario 3: The Marketing Manager
A 5:30 a.m. login from a known device. Password was once leaked, but changed three days ago.MFA is enabled. Not an admin. Not accessing critical systems.
On the surface, it looks suspicious. But when seen in context, it fits the user’s pattern; they’ve been catching up on work before a campaign launch. The system recognises the device, recent password change, and low privilege.
Access is allowed, no interruption, but maybe worth a check-in later.
Without context, all three logins would have looked identical. With context, you separate the attack from the anomaly, and the anomaly from the normal.
Why This Shift Matters
Every login tells a story. But most organisations only listen to the first sentence.
Context-based security lets you read the whole story before deciding what to do. It reduces false alarms, cuts alert fatigue, and transforms access control from a binary gatekeeper into a continuous risk evaluator.
And when context is paired with real-time SaaS visibility, you gain something powerful: the ability to understand the why behind every identity action, not just the who.
That’s how you move from reactive to predictive.
From chasing threats to recognising patterns.From managing users to managing behaviour.
The Takeaway
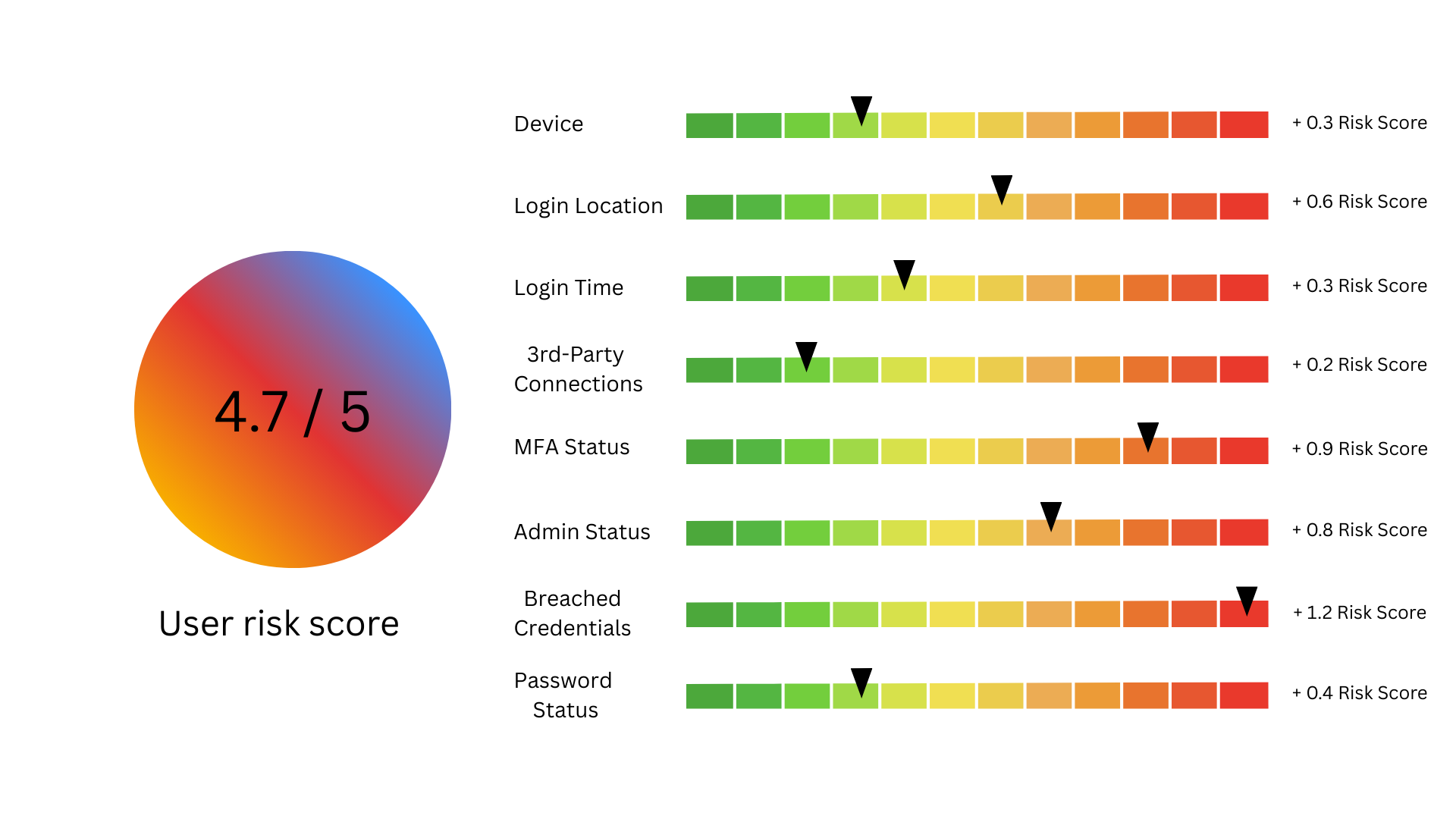
Context-based security doesn’t replace your identity systems. It elevates them. It’s what makes MFA, SSO, and IAM meaningful again, because you’re not trusting users blindly, you’re trusting their pattern of life.
At FrontierZero, we believe the next generation of SaaS security starts there. With context.With visibility.And with a clear understanding that not every login is equal, because not every story has the same ending.
See how it works in a live demo here.




