What SaaS Identity Sprawl Really Looks Like And How to Spot It Early
Your SaaS stack is packed with more identities than you think. From employees and vendors to bots and forgotten integrations—SaaS identity sprawl is a hidden risk most teams can’t see. We break down where it comes from, why it matters, and how to take back control.

What Is SaaS Identity Sprawl?
For every person in your company, there are likely 10 to 15 SaaS accounts tied to their name.
Now add contractors, vendors, bots, integrations, and AI tools—and suddenly, your SaaS environment has more identities than people.
SaaS identity sprawl is the unchecked growth of user accounts, access credentials, and third-party connections across your SaaS stack. Each identity carries its own permissions, authentication rules, and potential security risks.
Most of these identities are invisible to traditional IT and IAM systems—until it’s too late.
How Identity Sprawl Starts (and Spreads)
Identity sprawl isn’t always caused by negligence. It’s often a result of speed:
- New apps are adopted by teams without a security sign-off
- Admin rights are handed out temporarily and never revoked
- Integrations between tools spin up dozens of new identities in seconds
- MFA is enforced for core apps but skipped for peripheral ones
- Employees change roles, but their old access remains
- Service accounts, APIs, and AI tools quietly gain access to sensitive data
Over time, what began as productivity gains leads to a tangled mess of access rights and accounts—most of which no one is actively monitoring.
The Many Faces of SaaS Identity
Your SaaS environment includes more than just employees. Here's a quick breakdown:
Human Identities:
- Employees: Daily users with varying levels of access
- Contractors & Vendors: Often overlooked during offboarding
- Admin Users: High-value targets with extensive access rights
- Customer Support Accounts: Managed by vendors, but inside your stack
- Emergency Access / Break Glass: Rarely used, rarely monitored
Non-Human Identities:
- Service Accounts: Run background tasks and automations
- API Integrations: Connect tools and sync data across systems
- Bots & AI Agents: Perform actions, generate insights, and access sensitive data
- Partner Connections: Extend your SaaS stack into third-party ecosystems
Each of these identities comes with unique risks—especially when they are unmanaged, over-permissioned, or invisible.
Common Identity Risks We See
The impact of identity sprawl is not theoretical. It creates real-world risks:
- Dormant Accounts: Ex-employees or expired vendors with lingering access
- Privilege Creep: Users who accumulate permissions over time
- Overuse of Admin Rights: Too many high-privilege accounts, too little oversight
- Inconsistent MFA: Critical tools secured, others forgotten
- SaaS-to-SaaS Risk: Connected apps that inherit permissions without review
- Orphaned Identities: Service or bot accounts no one owns anymore
These risks grow silently and make it harder to enforce zero trust or least-privilege principles.
Best Practices to Control Identity Sprawl
You don’t need another policy document. You need real visibility. Here’s how to get control:
1. Build a Real-Time Identity InventoryUse identity-based scanning to see all accounts across your SaaS tools—including shadow identities and non-human ones.
2. Automate OffboardingMake sure accounts are automatically deprovisioned when employees or contractors leave—across every app, not just Google or Microsoft.
3. Audit Admin PrivilegesLimit who has elevated access. Monitor for privilege escalation and review admin roles regularly.
4. Enforce Consistent MFAApply MFA beyond just core platforms. Include CRMs, payroll systems, design tools, and AI integrations.
5. Track SaaS-to-SaaS IntegrationsUnderstand what third-party tools have access to your data. Review OAuth connections and integration scopes.
6. Spot Anomalies in Login BehaviorMonitor for off-hours logins, new devices, location mismatches, and brute-force attempts.
7. Manage Role Changes ActivelyWhen users switch departments or functions, review their access. Don’t let permissions accumulate.
8. Discover Shadow Identities EarlyUse tools that catch new accounts as they appear. Don’t wait for your next quarterly audit.
How FrontierZero Helps
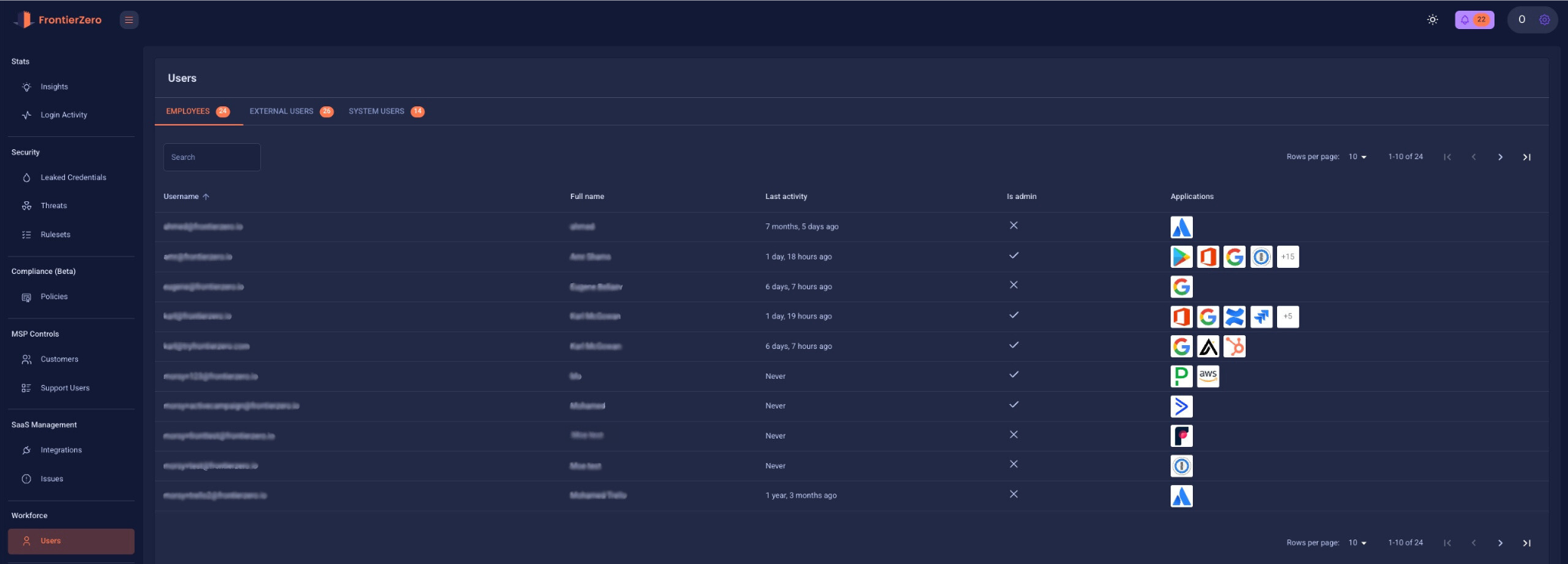
FrontierZero gives you a complete picture of your SaaS identity landscape:
- Continuous discovery of all human and non-human identities
- Visibility into orphaned accounts and admin roles
- MFA coverage monitoring across your entire SaaS stack
- Identity-level login behavior analysis
- Shadow app and OAuth integration detection
- Automated compliance reporting and access audits
Whether you’re trying to reduce attack surface or pass your next audit, we help you see what matters.
Final Thoughts
You can’t secure what you can’t see.
Identity sprawl is one of the most overlooked risks in SaaS security today. But it’s also one of the most solvable—when you have visibility at the identity level.
Want to get started? 👉 Start your free trial of FrontierZero




