Implementing 2FA is Step One — Here’s What Comes Next
Learn why implementing 2FA is a critical first step to protect your business, and how monitoring compliance is the key to preventing costly breaches.

Table of Contents
- Introduction
- The Reality of Cyber Insurance
- Implementing 2FA is a Great First Step, But…
- Imagine This: A Missed 2FA Setup Leads to a Breach
- Why You Need to Monitor 2FA
- The Bottom Line
Introduction
In today’s digital age, businesses face an array of cybersecurity threats, from phishing attacks to ransomware, and the consequences of a data breach can be catastrophic. With the average cost of a cyber breach sitting at a staggering $6.3 million, it’s no wonder companies are constantly searching for ways to strengthen their defenses. Implementing Two-Factor Authentication (2FA) is one of the most effective ways to protect your business. By adding an extra layer of security, 2FA can block over 99% of cyber threats. But here’s the catch: implementing 2FA alone isn’t enough—you need to monitor and enforce it, too.
The Reality of Cyber Insurance
Many businesses believe that having a cyber insurance policy will protect them in the event of a breach, but without proper security measures like 2FA, you might not be covered. In fact, cyber insurers are increasingly denying claims when they find that companies haven’t enforced basic security practices. Insurance providers argue that not having 2FA is negligent and could void the claim in the event of a cyber attack.
Imagine the impact: a breach happens, your company suffers millions in losses, and your insurer refuses to pay. The cost of the breach is only part of the problem. The damage to your reputation could be immeasurable, making it harder to recover customers and trust.
Implementing 2FA is a Great First Step, But…
It’s clear that 2FA is a powerful tool. It makes it exponentially harder for hackers to access your systems, even if they manage to steal user credentials. But there’s a problem. Many organizations think that once 2FA is set up, their work is done. Unfortunately, it’s not that simple.
Imagine This: A Missed 2FA Setup Leads to a Breach
Let’s say your IT department mandates that every employee activates 2FA on their accounts to comply with company security policies. You assume that everyone is following the rules—until one day, a breach occurs. Hackers manage to compromise one employee’s password through a phishing attack. Normally, 2FA would have stopped them in their tracks. But, as it turns out, this employee never activated their 2FA.
As the attackers move laterally through your network, accessing confidential files and sensitive customer information, you discover the damage too late. Millions of records have been exposed, and the financial and reputational fallout begins. Even worse, when you file an insurance claim, your provider denies coverage, citing negligence for not ensuring that security protocols like 2FA were enforced.
This scenario may seem hypothetical, but the lack of monitoring for compliance is a reality for many businesses.
Why You Need to Monitor 2FA
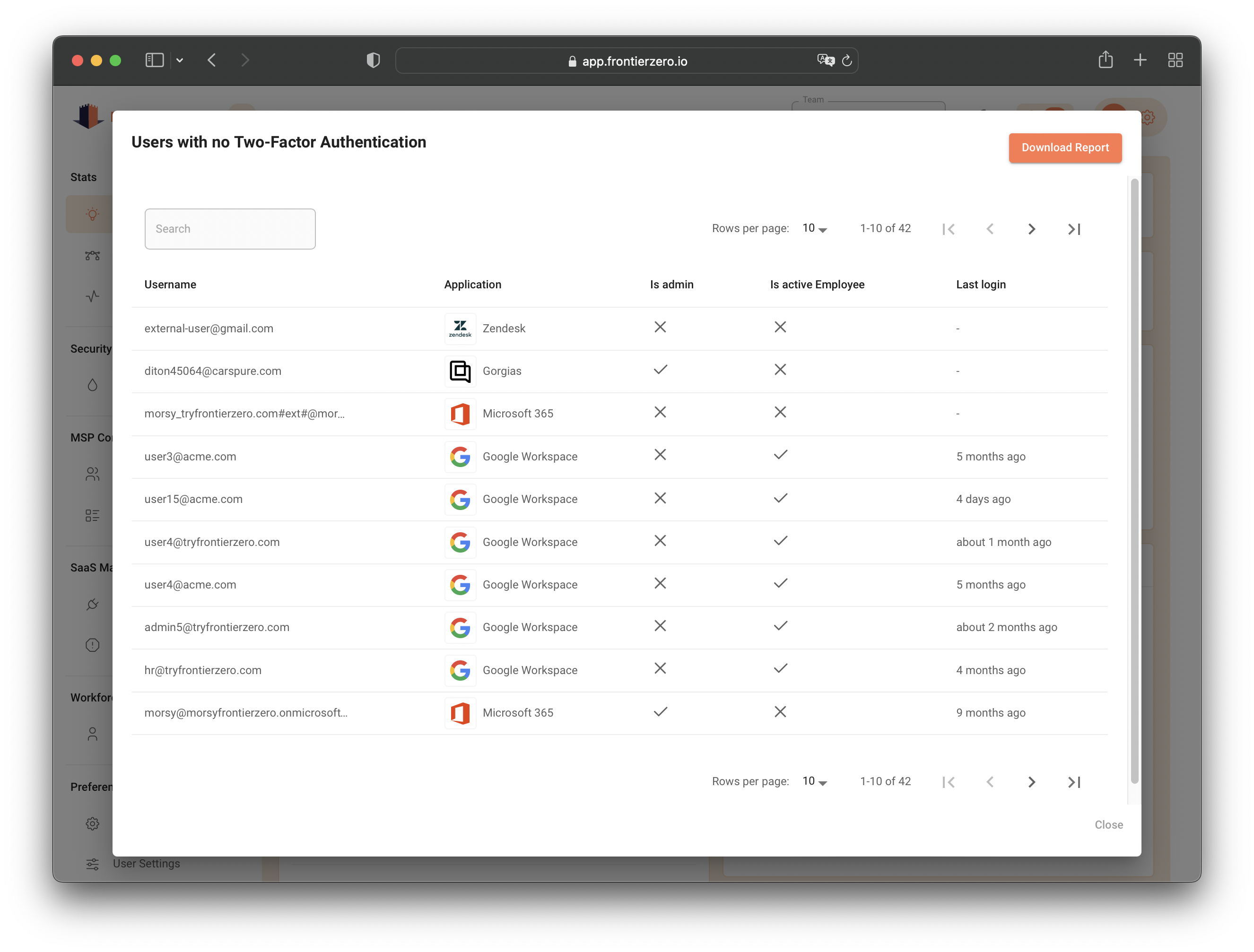
The truth is, people don’t always do what they’re told. Whether it’s due to forgetfulness, inconvenience, or a lack of understanding, employees may not activate 2FA even when required. Additionally, external vendors, contractors, or other partners who have access to your systems may not comply with your security policies.
Monitoring ensures that your 2FA is doing what it’s supposed to—protecting your business from threats. A 2FA monitoring tool helps you track who has enabled it, who hasn’t, and who is at risk of creating vulnerabilities in your system. It allows your IT team to take corrective actions before a small oversight turns into a massive breach.
The Bottom Line
2FA is essential for protecting your company against a multitude of cybersecurity threats. It dramatically reduces the chances of a successful attack by adding an extra layer of security. However, simply implementing it isn’t enough. To truly protect your organization, you need to enforce its usage and continuously monitor for compliance.
So, here’s the question: Do you know if all your employees and third-party vendors have 2FA enabled? If not, it’s time to start monitoring. Your cyber insurance, financial security, and reputation depend on it.




