Zero Trust for SaaS: Why Visibility and Access Control Are the New Perimeter
Today’s attackers don’t break in—they log in. Learn how Zero Trust helps organizations protect SaaS apps through continuous verification and least privilege access.
In today’s world, your perimeter isn’t your firewall. It’s your people. Your apps. Your identities.
And when 80% of breaches now involve stolen credentials, it’s clear: SaaS security has to start with Zero Trust.
But what does that mean when your employees use 300+ SaaS apps across multiple departments—and security teams have no clear visibility into who’s accessing what?
Let’s break it down.
What is Zero Trust for SaaS?
Zero Trust means: Never trust. Always verify.
Even if it’s someone inside your organization, on a familiar device, from a regular location—access still needs to be continuously monitored, verified, and restricted to only what’s necessary.
And in SaaS environments, this gets tricky.
People share logins.MFA isn’t enforced everywhere.IT doesn't even know what tools employees are using.
That’s the perfect storm for a breach.
Why Zero Trust Fails in Most SaaS Environments
Most Zero Trust frameworks are built for traditional infrastructure, not modern SaaS.
Here’s why they fall short:
- MFA is only enforced on Google or Microsoft—not on CRM, finance, or creative tools holding sensitive data.
- “SSO enforced” doesn’t mean the account is secure—users disable MFA or bypass controls.
- Login monitoring focuses on location or failed logins, but not behavioral patterns.
- Access isn’t revoked when employees leave or change roles.
- There’s no real-time visibility into lateral movement or overprivileged accounts.
The result?
Zero Trust on paper. Blind trust in reality.
The FrontierZero Approach to Zero Trust in SaaS
At FrontierZero, we help companies actually live the Zero Trust philosophy across their SaaS stack—with visibility, monitoring, and control.
Here’s how:
1. Enforce MFA—Everywhere
Zero Trust starts with verifying users. That means enforcing MFA not just on Microsoft or Google—but also on:
- CRMs
- Finance tools
- Developer platforms
- Admin panels ...anywhere sensitive company or customer data lives.
✅ FrontierZero monitors MFA status across all critical apps✅ Flags accounts that don’t meet your policy✅ Alerts you when MFA is disabled—or never turned on in the first place
2. Monitor Logins and Patterns of Life
Most attacks don’t look suspicious at first glance.That’s why we go beyond IP addresses.
With FrontierZero, you monitor:
- Devices employees usually use
- Times they usually log in
- Locations they typically access from
When behavior shifts—like a 3AM login from a new device in a new country—we flag it.Before attackers escalate.
3. Catch Exposed Credentials on the Dark Web
Credentials from Oracle.Logins stolen in the Snowflake breach.Even personal accounts reused at work.
FrontierZero continuously monitors the dark web for your organization’s emails and credentials.If something leaks—we alert you instantly.So you can lock down accounts before attackers get in.
4. Enforce Least Privilege Access
Zero Trust isn’t just about blocking bad logins.It’s about limiting what users can do—even when they’re logged in.
FrontierZero flags:
- Overprivileged accounts
- Admins accessing tools they don’t need
- Risky privilege escalations
You get the insights to reduce access risk—and the control to de-escalate immediately.
Final Thoughts: You Can’t Trust What You Can’t See
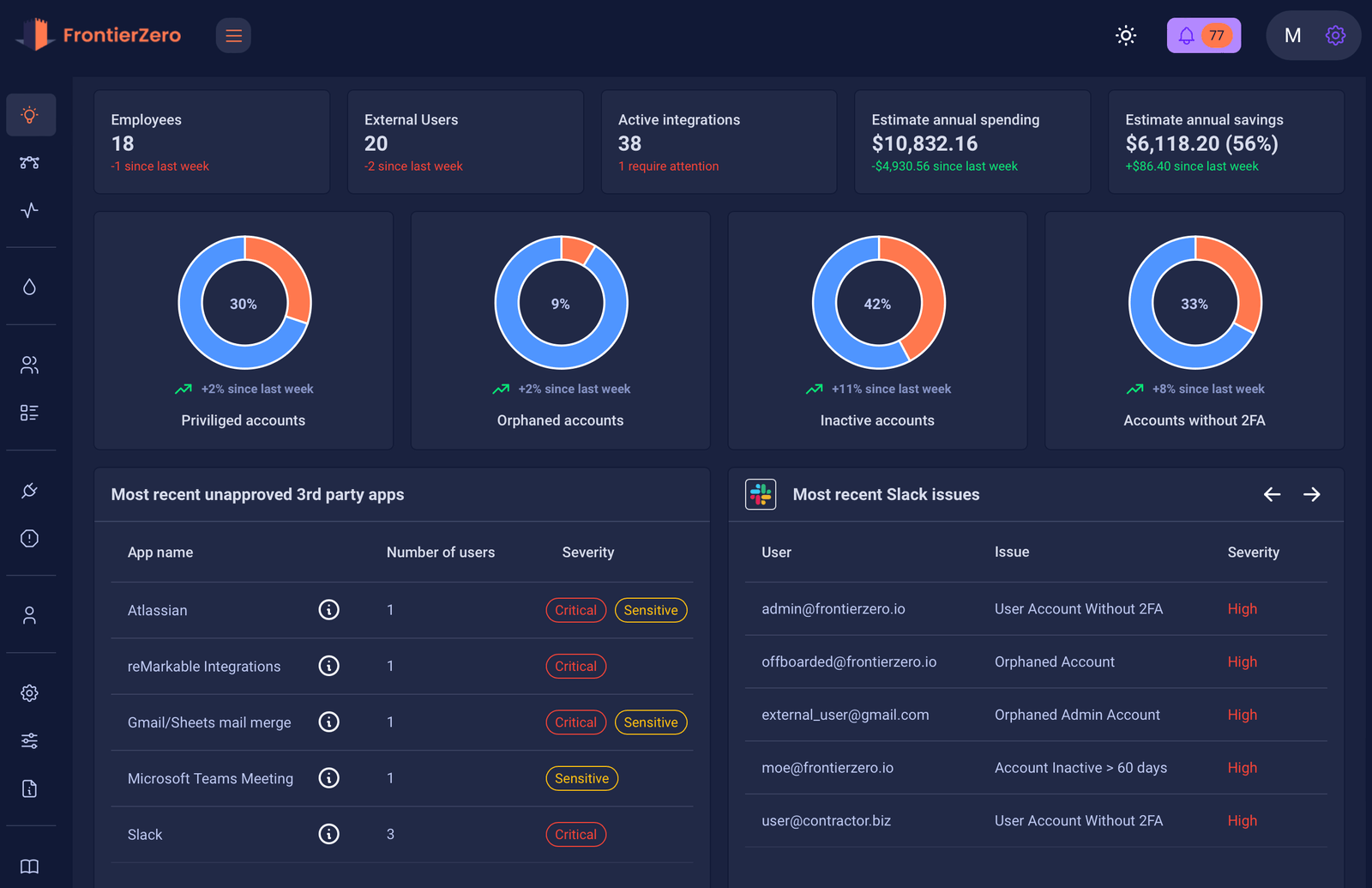
Zero Trust for SaaS isn’t just about better policies.It’s about better visibility.
Because breaches don’t always start with code.They start with a login.
If you’re ready to enforce Zero Trust across your SaaS apps—without adding more complexity—FrontierZero helps you get there in under 15 minutes.
Or get in touch with our team to see how we help organizations protect identities, monitor logins, and enforce Zero Trust at scale.




